APKey
This app contains some unique keys. Can you get one?
APKey
This app contains some unique keys. Can you get one?
Firstly, install the app to inspect the activity main page.
However, face difficulties with installing through adb prompt will following errors:
`adb: failed to install backup.apk: Failure [-124: Failed parse during installPackageLI: Targeting R+ (version 30 and above) requires the resources.arsc of installed APKs to be stored uncompressed and aligned on a 4-byte boundary]
After some research, we have to align the packet in bytes of 4 using zipalign.
$ zipalign --help |
when trying to launch zipalign from kali linux, I have problem with error for the packet. After more research.
zipalign
Manage to download the right package from this site.
perform dpkg -i <package.deb>
When installing we are missing android-libandroidfw package.
$ sudo dpkg -i zipalign_8.1.0+r23-2_amd64.deb |
Performa a install on the package
sudo apt-get install android-libandroidfw |
And now we got our zipalign working
$ zipalign -p 4 APKey.apk zipalign_APKEY.apk
Next we can perform a check if the APK is aligned with 4 bytes
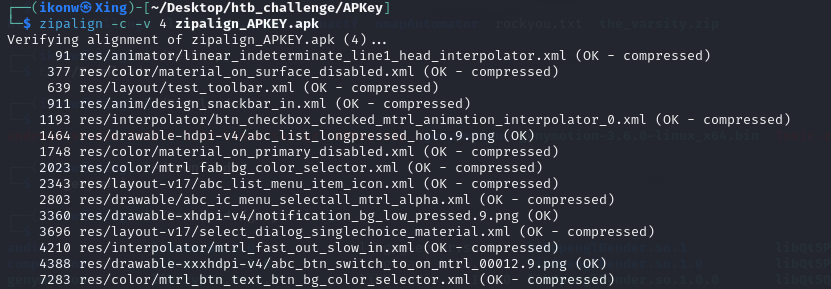
Good!
After realign the APK, we have to sign the application again using apksigner with the fake private key
keytool -genkeypair -v -keystore my-release-key.jks -keyalg RSA - keysize 2048 -validity 10000 -alias my-alias |
apksigner sign --ks my-release-key.jks zipalign_APKEY.apk |
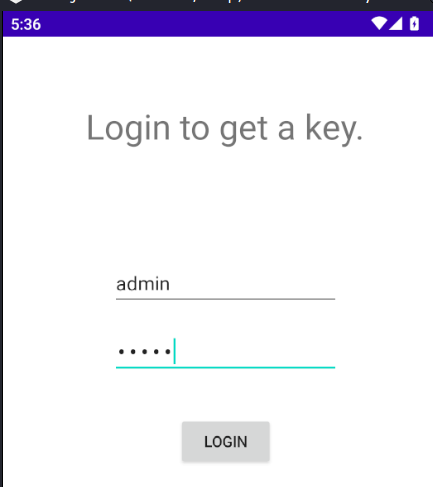
Manage to install the application sucessfully this time round.
The application requires a authentication for a key.
Decompile APK
Decompile the application with apktool
apktool d apkey.apk
Also open it using jadx-gui
Inspecting at the manifest file, found the launcher is at MainActivity
|
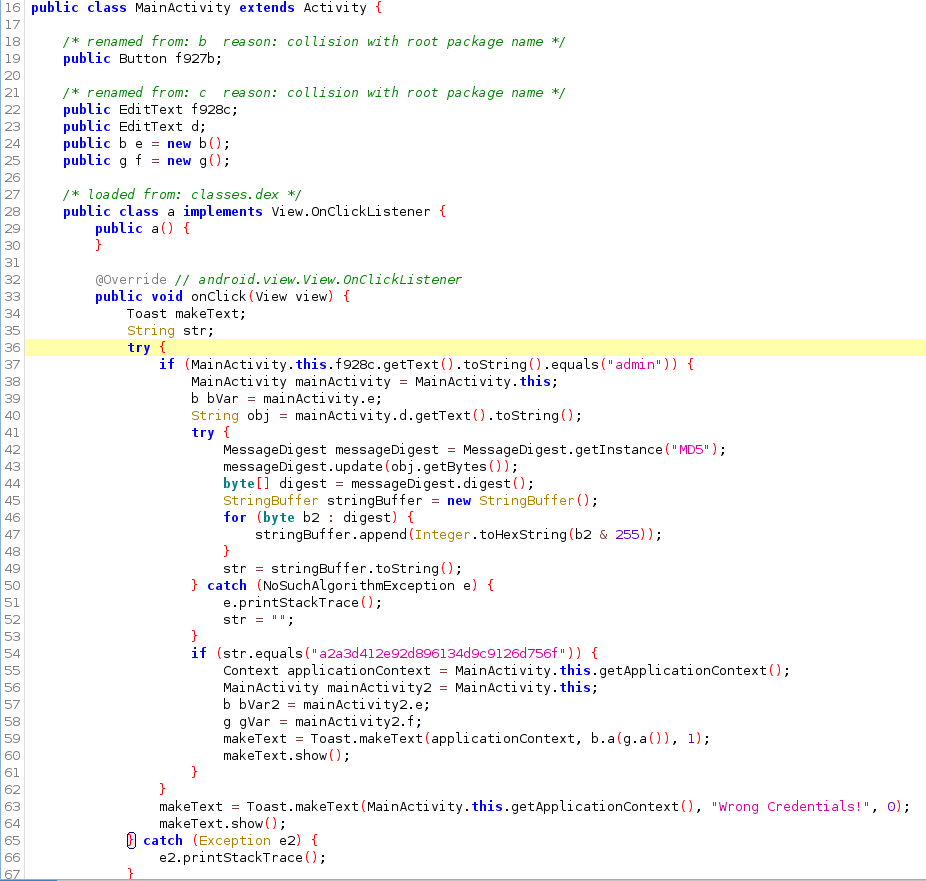
As from the previous section, we notice that the login page requires 2 input box, username and password. It is declare at line 22 and 23 with object EditText
This is further prove by if (MainActivity.this.f928c.getText().toString().equals("admin")) {
which it is checking if the user input for f928c is equal to admin. Next it create a MD5 object and hash the user provided password and check if it is equal to a2a3d412e92d896134d9c9126d756f.
However this hash is uncrackable.
Since it is a simple logic of EQUAL , we can modify the smali code to become NOT EQUAL.
but first, we have to allocate where is the comparison in smali.
From the apktool decompile folder, navigate to smali/com/example/MainActivity$a.smali
About line 141, we saw the hash a2a3d412e92d896134d9c9126d756f
:try_start_2 |
A sample of code near the hash, we can see that the second line
invoke-virtual {p1}, Ljava/security/NoSuchAlgorithmException;->printStackTrace()V
is actually the printStackTrace function
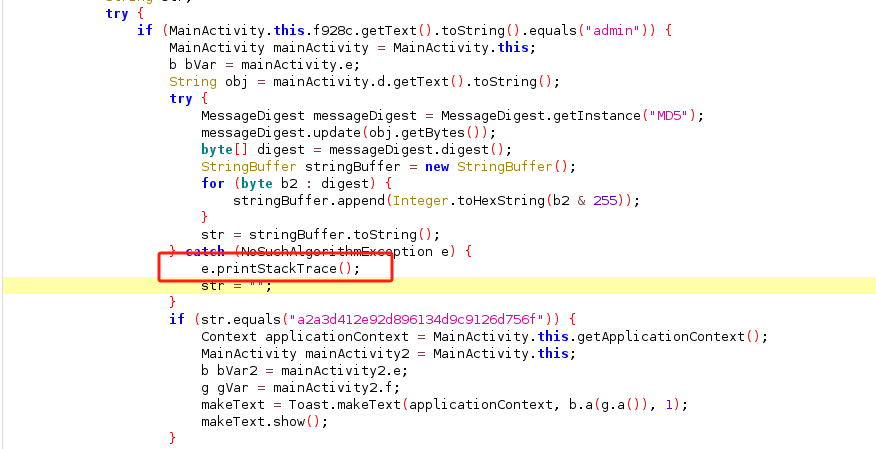
corresponding to the red box.
const-string p1, "" next it set the p1 register to an empty string.
:goto_1 seems a JUMP label which if refer to the code, it is the end of catch.
const-string v1, "a2a3d412e92d896134d9c9126d756f". next it set the V1 register.
On a side note, was curious if the register stored the address or the actual value.
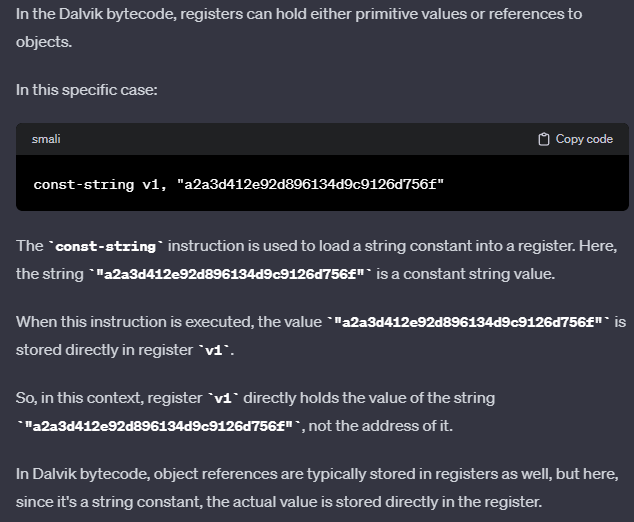
http://pallergabor.uw.hu/androidblog/dalvik_opcodes.html
after that it perform equal function with the string and the hash
invoke-virtual {p1, v1}, Ljava/lang/String;->equals(Ljava/lang/Object;)Z
This equal function takes in 2 parameter, and return a boolean Z
move-result p1 next it move the boolean result into p1.
if-eqz p1, :cond_1 check if P1 is true, then it jumps to label cond_1
Which this is the critical statement that wanted to change,
with a little bit help from CHATGPT.
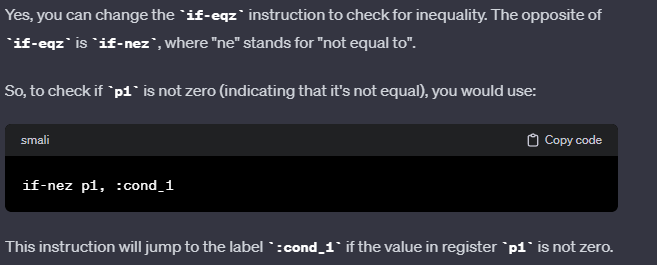
Good, we have the code now, let’s save the changes.
Compile the samli app using apktool
$ $ apktool b APKey |
Zipalign the 4 bytes and sign again
$ zipalign -p 4 APKey.apk zipalign_APKEY.apk |
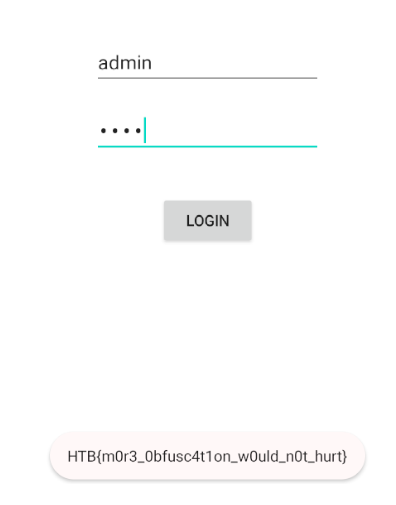
Type random password, will result in not equal the hash and it actually print the flag.